WordPress security should be one of the first concerns for anyone with a website. Every week Google blacklists 20,000 sites for malware and 50,000 for phishing. If you work on your website, you need to pay attention to the security of your website. In this article, we are going to share with you the best systems to protect your WordPress website against hacking and malware attacks.
WordPress core, in contrast to what many people say, is very secure and is constantly reviewed by hundreds of developers. Usually the biggest vulnerability of WordPress is actually the user who due to wrong practices creates problems to WordPress security.
In this article we are going to see what we can do to avoid creating vulnerabilities in our WordPress site and what we can do to make our WordPress installation even more secure.
Table of Contents
Is WordPress safe?
According to statistics from Sucuri, a company working in the field of online security, 83% of the infected sites they have worked with are WordPress sites.
Of course, we have to take into account that WordPress is the foundation used to build 33% of the websites on the internet. Also, it is not a surprise that vulnerabilities exist since there are thousands of WordPress themes and plugins on the market.
The WordPress community is very active and the “WordPress Security Team” counts 50 security experts who constantly work to keep the famous CMS secure.
The most common problems that lead a site to be hacked are usually due to bad practices on the part of the user or the hosting. In one of the following points, we will see what SupportHost does to protect your website to the fullest.
These practices include:
- use of old versions of WordPress with known vulnerabilities
- use of invalid themes and plugins
- incorrect system administration
- poor management of login credentials
- Lack of technical knowledge from the user leads him/her to make simple errors
Why is WordPress security important for your site?
If your site gets hacked your business suffers, but so does your reputation. Hackers can steal information about your users/customers, steal passwords, install malicious software or distribute malware to your users.
In some cases, you may find yourself having to pay a hacker to gain access to your website again.
In light of the numbers I mentioned above, if your site represents your business and you use it to create income you need to pay special attention to the security of your WordPress installation.
What is security?
La sicurezza non è un concetto assoluto ma un processo Safety is not an absolute concept but a continuous process, and it must be characterized as such. It is not possible to eliminate risk, this is never going to be zero, but we can reduce it to a certain extent.
Security is not only about WordPress, but you have to secure your local environment, the processes you use and what you do online as well. Security is divided into three areas: people, processes, and technology. These three areas must work in synergy to ensure maximum security.
Basic Security Concepts
There are some basic security concepts you should be aware of before venturing into the topic we’re about to cover in detail: WordPress security. These concepts are critical to understanding and implementing the steps outlined in this guide.
Least Privilege Principle
When configuring a web application, in our specific case WordPress, each application or user must be able to access only the resources they need, and nothing more. In other words, we should not give permissions greater than what a user needs. For example, if a user on your blog only needs to edit posts, it doesn’t make sense to give him administrator privileges.
The Least Privilege Principle involves providing individuals with the minimum access required to perform their function and only for the time needed to accomplish their job. Once the job is complete, access must be restored to an appropriate level. WordPress already has default user roles, each with different privileges/permissions, making it easy for you to assign each user the necessary privileges.
Deep Defence
This idea is based on the fact that there is no single solution for all security problems. Therefore, it suggests the use of an approach with complementary layers designed to cover the deficits of the other layer. By using multiple layers of security, if one of these security measures is exceeded the hack is blocked at the next layer, or at least slowed down and discovered in time. Using such layered security results in a solution such as: using a firewall to mitigate external attacks, using a security scan to detect and block those attacks that get past the firewalls and using different types of authentication.
Security under control
Let’s go beyond theoretical concepts and use these checks in practice. To protect our site for WordPress security we will stick to the following points:
- Limit access: minimize the number of people who have administrative access to your website. You should also minimize the number of “entry points,” meaning delete all web applications you don’t use and remove themes and plugins you don’t use.
- Functional isolation: your system should be set up to minimize the damage that can be caused if it is compromised. With SupportHost all accounts are isolated, so it is not possible to attack another account from an infected one. It is recommended to avoid using different applications on the same hosting account (for example we have the customer area on a different domain, so if our WordPress site gets hacked our customers’ data is safe elsewhere). If you use one hosting account per site the damage would be limited to one website.
- Backups: keep up-to-date backups for your website. With SupportHost you are safe since we maintain 30 daily backups for each account. It is important to have a plan to recover your website in case it is compromised.
- Keep everything updated to the latest version: you must do everything possible to keep everything updated to the latest version. We’re talking about the WordPress core, the themes and plugins you use, but also making sure your provider keeps the server operating system and all the control panels up to date with the latest version.
- Trusted sources: don’t download any themes or plugins that are nulled or from sources you can’t trust 100%. Using a nulled plugin is a recipe for disaster. There are people who distribute nulled plugins and themes with malware for the purpose of breaking into your site and using it.
- Security Updates and News: Security holes are a problem in any software and WordPress is not immune. Stay up to date by subscribing to the WordPress vulnerability database maintained by WPVulnDB.com or by following the security category of the WordPress blog.
Work in a Safe Environment
You also need to be sure that the environment in which you work is safe. Keep your computer software, browsers and routers up to date, and check them periodically with appropriate software for viruses, malware or spyware. Consider using a secure VPN to encrypt all your online communications when using public connections.
Types of Vulnerabilities
Since WordPress is an open source platform, anyone can contribute to its development. This makes it easy to find developers to create themes and plugins and offers more and more features to users.
However, it is this openness that leads to security issues that cannot be ignored. Every plugin and every theme that is created can contain vulnerabilities. There are different types of vulnerabilities. Let’s have a look at them one by one.
- Brute Force attacks
- SQL Injection
- Malware
- Cross-Site Scripting
- DDos Attacks
- Outdated versions of WordPress and PHP
Brute Force attacks
Brute Force attack is nothing more or less than a series of attempts to discover a password. Basically, a bot tries different combinations until it finds the correct user and password. Usually algorithms and dictionaries are used to try to guess the most common passwords.
This type of attack is difficult to execute but still remains common. WordPress does not block repeated login attempts so a bot can try thousands of combinations per second. At SupportHost we have a security system in place to protect our users from this type of attack, which we will discuss in the next chapter.
Prevent and block this kind of attacks
To avoid this kind of attacks (in addition to our protections) it is advisable to use long passwords that contain uppercase, lowercase, numbers and symbols, for example using special keyboard characters. Another good practice is to use a username other than admin for login, this is the most common username and the one that is mainly used for this kind of attacks.
If we want WordPress security another good practice is to use two-factor authentication, which we’ll talk about in more detail later.
SQL Injection
This is one of the oldest methods of hacking a website and consists of injecting an SQL query using a form in order to corrupt the database.
After performing the intrusion the hacker can manipulate the MySQL database and get admin access or change login credentials. This type of attack is usually performed by amateur hackers who want to test their skills.
Prevent and block this kind of attacks
You can use a plugin to check if your site has been a victim to this type of attack. Two great plugins to do such a check are WPScan and Sucuri SiteCheck.
At SupportHost, we use Imunify 360 which allows peer-to-peer scanning without affecting the site’s performance. Indeed, security plugins are among the plugins that slow down WordPress. These plugins should be avoided because they have a pretty big impact on performance, and they do a job that the server if managed properly and with the right software, does the job more efficiently.
Malware
In this case, a malicious code is injected into your WordPress installation using an infected theme, or an old version of a plugin. This malware can be used to extract data from your site or insert content undetected.
Malware can cause various types of damage, from adding links to your site’s content to infecting the core of your WordPress installation.
Preventing and blocking this kind of attacks
Usually it is the user himself who infects his site by using nulled themes and plugins (aka cracked versions). A golden rule to secure WordPress and protect your site is to make sure you download themes and plugins for your website only from safe sources. There are people who buy premium themes and plugins and distribute them for free after introducing malware inside them.
Plugins such as Sucuri or WordFence can run a scan and discover malware.
In the next chapter we will see how we protect SupportHost customers from this kind of threat.
Cross-Site Scripting
One of the most common attacks is Cross-Site Scripting also known as XSS attack. In this case, the attacker uploads a JavaScript code that when executed by the client’s browser collects data and in some cases performs a redirect to a malicious site.
Prevenire e bloccare questo tipo di attacchi
To prevent this type of attack you need to validate the data that is entered into your WordPress site through sanitization. This is done directly by themes and plugins, sanitization is done through code. You can use a plugin like Prevent XSS Vulnerability to protect yourself.
DDos Attack
A Distributed Denial of Service (DDoS) attack is a more advanced version of a Denial of Service (DoS) attack. This type of attack involves making enough requests to cause problems for the web server.
While DoS attacks use only one source (and are therefore easier to block) DDoS attacks are launched from multiple locations (hundreds or thousands of IPs visiting simultaneously) and are therefore more difficult to block.
Prevent and block this type of attacks
At SupportHost we have advanced DDoS protection which we will discuss in detail in the next chapter. To prevent this kind of attacks there is very little you can do yourself for WordPress security, but you have to trust the measures put in place by your hosting provider.
Just recently a famous Italian provider went under a DDoS attack leaving all its users offline for days, a situation that could have been avoided if they had advanced protections in place for this type of attack.
Obsolete versions of WordPress and PHP
Older versions of WordPress are easy to hack as they contain known vulnerabilities. WordPress continually releases versions with security updates for this very purpose.

The same can happen if you use an old version of PHP, which can have security holes, or cause incompatibility issues. Since WordPress uses PHP, it needs an updated version of PHP to run smoothly.
According to official WordPress statistics 42.6% of users use an old version of WordPress and only 2.3% of WordPress sites use the latest version of PHP, which at this moment is 7.2.
Prevent issues like this
This one is very simple. To avoid vulnerabilities of this kind you have to stay away from outdated versions, which means that in order to establish WordPress security and keep it that way, all you have to do is keep WordPress and the plugins and themes you use up to date.
As for PHP and all the software on the server you don’t have to do anything, since your provider takes care of that. With SupportHost you can choose which version of PHP to use, and we keep all the software on the server always updated to ensure maximum security.
All you have to do is follow our tutorial to change the version of PHP after making sure that the plugins and themes you use are compatible with the latest version available.
Hosting and Security
The first level of security must be provided by the provider. No matter what you do, if your provider fails to maintain a secure environment for your website and is unable to protect you from the most common attacks you will never have a secure site and any attempt to secure WordPress will be in vain.
In our WordPress hosting we have several systems in place to protect our customers’ sites, let’s see them in detail.
Anti-DDoS Protection
What is a DDoS attack?
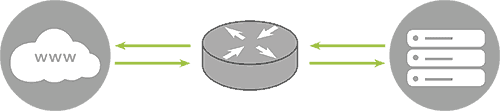
A distributed denial-of-service (DDoS) attack is a type of attack that involves overloading a server, service, or network with a flood of traffic from multiple sources. DDoS attacks derive their efficiency from using multiple traffic sources, sources that have been previously compromised for this purpose. A DDoS attack is like a busy highway, so busy that normal traffic cannot get to its destination.
How a DDoS attack works
The first requirement of a DDoS attack is that the hacker has control of a network of online machines in order to direct the attack. These are infected with malware so that they can be used as a bot. The attacker then has control over these machines (bots), this network is called a botnet. Once the botnet is created the attacker provides instructions for the remote attack. Once the victim’s IP is decided each bot sends requests causing an overload that results in an inability to offer service to normal traffic. Since each bot appears as normal traffic it is difficult to separate attackers from normal traffic.
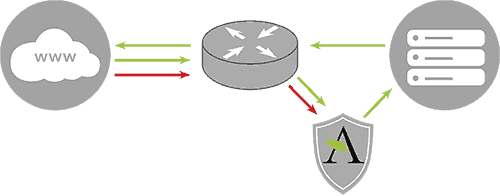
SupportHost’s solution to DDoS attacks
SupportHost uses automated tools to protect customer applications, sites and servers from this type of threat. Our automated prevention system recognizes almost all of these attacks in advance, allowing us to catch them in the early stages and thwart these types of attacks before they can create disruption to our customers. We protect our customers with Arbor and Juniper hardware.
data transmission during a DDoS attack
Automatic Attack Pattern Recognition
In addition to recognizing the attack based on the amount of traffic received, SupportHost is able to define the type of attack and react appropriately to each type of attack to prevent it. For example, a UDP flood with 500k pps does not create any problems for the server, while a 500k SYN packet could create problems. Our DDoS protection can detect the difference between the two and react accordingly.
Traffic filtering based on known attack patterns
This method allows us to automatically filter out known attack patterns and pass this traffic through our filters. This method is especially effective for the following attack types: DNS reflection, NTP reflection, and UDP floods on port 80.
Challenge-Response Authentication and Dynamic Traffic Filtering
In this last layer we filter SYN floods, DNS floods and invalid packets. We are also able to flexibly adapt to other types of attacks in order to mitigate them. These technologies allow us a high level of automation, automation that is constantly updated and optimized. We are constantly improving the system so that filters and responses are optimized.
What it means for customers
Our DDoS protection does not affect the prices we offer our customers. Our system recognizes DDoS attacks and its ability to recognize them improves over time. Once the attack is recognized, our dynamic DDoS protection goes into action filtering out the attack. Your traffic will not be affected by our dynamic protections to mitigate the attack.
Antivirus
ClamAV is an open source antivirus software that is used to identify trojans, viruses, malware and other threats by relying on automatically updated data via the internet.
We use ClamAV to scan all incoming and outgoing emails on our servers to ensure that you can neither send nor receive viruses or anything else through our service.
You can also run antivirus scan on your account yourself by following our tutorial.
Anti-Malware
We automatically run an Anti-malware scan on all files the moment they are uploaded to the server.
The software we use for this purpose is Imunify360. Active file scanning can help prevent malware from exploiting an account by deleting or moving suspicious files to quarantine before they become active. It can also prevent the loading of PHP and perl shell scripts, which are commonly used to launch multiple malicious attacks and send spam.
Imunify360 also allows you to perform on-demand scans of files, directories and user accounts for suspected exploits, viruses and suspicious resources (files, directories, symlinks, sockets). You can perform scans of existing user data to check whether exploits have been loaded in the past or via methods not covered by active scanning.
Antispam
SpamAssassin is configured on all SupportHost servers. This is an anti-spam software that filters incoming spam mails using context-based rules but also rules based on DNS, checksums and statistical filtering.
SpamAssassin is considered to be one of the most effective spam filters, especially in our case since we use it in conjunction with an antispam database.
For most users a simple text comparison is enough to filter out most of the mail they receive.
Firewall
On all SupportHost servers we have installed a Firewall. ConfigServer Firewall, also known as CSF, is a firewall configuration script created to provide enhanced security for the server. CSF configures the server’s firewall to block public access to services and allow only certain connections, such as accessing FTP, checking email, or uploading websites.
Intrusion Detection System
ConfigServer Firewall comes with a service called Login Failure Daemon, or LFD. LFD monitors user activity for excessive login errors that are commonly observed during brute force attacks. If a large number of login errors come from the same IP address, that IP will immediately be temporarily blocked from all services on your server. These IP blocks will automatically expire, but can be manually removed by our operators. In addition to removing IPs, CSF also allows you to manually whitelist or blacklist IPs in your firewall, this way we can prevent some particular IPs of our clients from being banned by the firewall.
We have also set up proprietary rules to mitigate the most common brute force attacks on major CMSs. For example if you try to login to WordPress repeatedly with incorrect data your IP address will be blocked for half an hour. This helps us to maximize the protection of our users from brute force attacks while keeping WordPress or other CMSs they use safe.
Total Account Isolation
One of the ways we use to keep our clients’ accounts as secure as possible is by completely isolating each individual account. You may think that shared hosting on most services is secure and that access to your account is yours alone. Unfortunately, in most cases this is not the case.
Shared hosting providers often have security issues that can cause problems for the entire server, and this happens because simply one of the accounts on that server has an insecure application. The majority of open-source software, such as Joomla, WordPress and many other applications are favorite targets for hackers. On a standard shared server when one of these vulnerable accounts is attacked, the hacker can easily attack all the other accounts on the same server, or even take the entire server offline.
We get endless requests from potential customers asking if our service is secure because their account has been hacked multiple times with another provider.
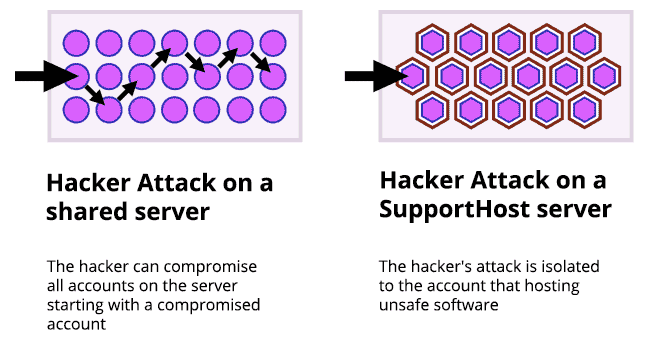
On our secure hosting we use a custom chroot isolation technology. With our solution even if one account is not secure, the other accounts on the same server cannot be attacked via the web server or cron like in a normal shared environment.
This makes us one of the most secure hosting, you can sleep soundly knowing that your site is on one of the most secure platforms on the market.
Protect WordPress
Keep WordPress Updated
When it comes WordPress security this is perhaps the advice that goes by the most, and there’s a reason why. Automaticc (the company behind WordPress) and plugin and theme developers periodically release new versions in order to close those security holes that are periodically discovered. WordPress can automatically update itself for security updates, while it requires manual updating for major updates that might cause plugin incompatibility.
The same goes for themes and plugins. An outdated theme or plugin can be a weak point that allows a hacker easy “entry”.
Install a Backup Solution
Backups are your first defense against a hacking attack. Remember that nothing is 100% secure and if government sites and bank sites get hacked yours can get hacked too. Backups allow you to restore your site to a previous version without losing anything in case something happens.

Not all hosting services offer a professional and usable backup solution. With SupportHost you have 30 daily backups available at any time. That is to say, if your site has been hacked you can choose from 30 different backups to restore it.
If your hosting does not provide an adequate backup service there are several plugins that allow you to create a backup copy and save it on an external server. We recommend UpdraftPlus even if it would be smarter to change hosting to a provider that offers a professional solution for backups.
Change Database Prefix
The vast majority of WordPress installations use the prefix “wp_” before each table name. If your site also uses this prefix you are making life easy for hackers who can guess the prefix of your tables. Let’s see now how changing it helps us secure WordPress.
If you are doing a new installation you can choose a different prefix during the installation process, in the screen where you are asked for your database access data.
If you already have WordPress installed and want to change the prefix of your tables there will be some manual work to do. Alternatively you can use a plugin like “Change Table Prefix”. Always remember to make a backup of your website before proceeding with such operations, so that you can go back in case there is some problem with the changes.
Change Security Keys
WordPress uses security keys, which are stored in the wp-config.php file, to encrypt session data that is stored in cookies in the browser. These keys are called Keys and Salt.
You can change these keys at any time. It is recommended to change them before installation and then change them periodically. Changing these keys regularly allows you to invalidate active sessions and force all your users to log in again. You can generate the keys manually, but we recommend using the official WordPress service to replace the keys with the ones already in the wp-config.php file.
Locking the administrator part
There is a strategy for security that is called security by obscurity. This strategy is very effective for an average site. If hackers can’t find your login page, it’s harder for them to attempt an attack.
To achieve this armoring let’s proceed by changing the login url and limiting the number of login attempts. As I explained before on SupportHost we limit with proprietary rules the number of logins for the main scripts, so these rules also apply to help you secure WordPress. However, if you decide to change the login url our system will stop working and you will have to use a different system.
#How to change login url
By default your admin area is located at dominio.it/wp-admin while login page is located at dominio.it/wp-login.php.
The problem with this system is that even hackers and bots know this. By changing the url you make life more difficult for those who want to attack you, it is difficult to launch a brute force attack if you don’t know the login url.
To perform this operation we recommend the WPS Hide login plugin. You can change the login url easily from settings, but remember to choose a name that is not already in the list that bots or hackers might find.
In this case you will need to use a plugin to set a limit of login attempts. Let’s see how to limit logins by setting a maximum limit of attempts and thus secure WordPress.
How to limit login attempts
At this point, our protection will no longer work to protect you from hacker attacks. Our rules to limit login attempts use urls, so if you change address we won’t be able to identify and block an attack.
In this case you will need to use a plugin to set a limit of login attempts. The free Cerber Limit Login Attempts plugin is great for setting the block duration, maximum number of login attempts and creating IP whitelists and blacklists.
Using HTTP authentication
Another way to protect your restricted area and secure WordPress is to use HTTP protection. With this type of protection you are prompted for a username and password even before accessing the WordPress login page. This type of protection can’t be used on sites that allow users to access the private area (otherwise we’d have to give everyone a double login) but it’s a great way to reduce the number of “hits” by bots.
On SupportHost you can add this kind of protection directly from cPanel. To protect a folder with password you can follow our tutorial “how to protect a folder with password“.
Using a Web Application Firewall
If you use CloudFlare or Sucuri you can block a url. Basically you can set a rule so that only your IP address can access the admin area. Also this solution cannot be used on sites that allow users access to the restricted area.
CloudFlare offers this service in its Pro accounts or higher levels by which you can set a rule for each url.
Sucuri offers a feature called Blacklist URL path feature, and you can then set your IP to whitelist.
Choose Reliable Plugins and Themes
Plugins help you extend the functionality of WordPress while themes help you modify the graphical interface of your website to your liking. There are hundreds of thousands of plugins and themes, you can find them in the official repository and hundreds of other places.
You often install plugins and themes quite lightly, but these can lead to security issues. As I explained in the Security Under Control section downloading a nulled plugin can lead to problems, there are people who on business distribute nulled plugins and themes with malware in order to break into your site and use it as they please.
But besides these intentional cases, you can download a plugin that has a security hole, that’s exactly why continuous updates are released for plugins and themes to close these security holes when they are found.

WordPress Security means paying attention to any flaws as well, that’s why it is of utmost importance to download only plugins and themes from the official WordPress repository or reliable websites. Before choosing a theme or plugin you should always follow these steps:
- Check reviews, number of downloads and comments
- Check the date of the last update to see if the software is still active or has been abandoned
- Search by author and see what other themes or plugins are active in the repository
- Check if the theme or plugin is compatible with the version of WordPress you use.
Obviously always backup your website files and your database before proceeding with the installation. This way if there are any problems you can always go back easily.
Protect Login
As we have seen a very common type of attack is Brute Force attack. Let’s see what we can do to achieve WordPress security and protect our site from this type of attack.
Choosing the User Name
First of all, if you are using “admin” as a username for your admin account, change it to any other name immediately. Most brute force attacks use this very username to try to gain access with random passwords.
Also, you should make sure that your username is different from the displayed name. The idea here is to not let people who want to attack your website know what your admin username is. If you post articles with your name, and the same name is the admin user you have just provided useful information to those who want to undermine the security of your website.
In this case there are two things you can do:
- Use a different username than the name under which you publish articles, but keep in mind that you will always be able to see your username in the author page link
- Create an editor account that you will only use to post on your website. This way even if people come in using your editor account they won’t be able to do much since they won’t have the necessary permissions.
Use a Password that’s not very common
From a research the most used passwords are ‘123456’, ‘qwerty’, ‘letmein’. In 2015 ‘starwars’ was in the list of 25 most used passwords. Using such a password is equivalent to writing the pin number on your credit card.
You should use a long, complex and unique password. So that it contains 16-20 characters, upper case, lower case, numbers and symbols and can’t be guessed by checking a vocabulary.
There are online tools that create a secure password for you. Of course you have to save it, for example in the browser or using tools like LastPass or 1Password.
Please note that our proprietary rules mitigate brute force attacks, but this does not mean that you should use a weak password that is easy for an attacker to discover.
Using Two-Factor Authentication
Even if you’re not using ‘admin’ as your username and your password is long and complex, you could still be the victim of a brute force attack. We limit login attempts to major CMSs to 5 every half hour, but if the attacker has multiple IPs they could still discover your login details.
To limit this kind of problems as much as possible in certain cases (e.g. if you manage sensitive customer data) it may make sense to enable two-factor authentication.

We know how tedious two-factor authentication is, but in some cases it’s necessary. Of course if you have a simple blog and no customer data is stored it’s additional security but not necessary in this case.
There is a plugin to secure WordPress with two-factor authentication: Google Authenticator.
Automatically log off inactive users
Logged-in users can wander away from the screen and this could pose a risk. Someone can log in using a method called “session hijack” and change the user’s password or make changes to their account.
This is exactly why most sites on which you manage money (PayPal, banking sites) automatically log out inactive users after a certain amount of time. You can implement a similar feature to secure WordPress.
You can use the Inactive Logout plugin and after activating it set the message for users and the maximum inactivity time to logout inactive users.
Disable Login Suggestions
When you login with incorrect data WordPress returns an error on the login page, indicating whether or not the username exists or if the problem is due to incorrect password.
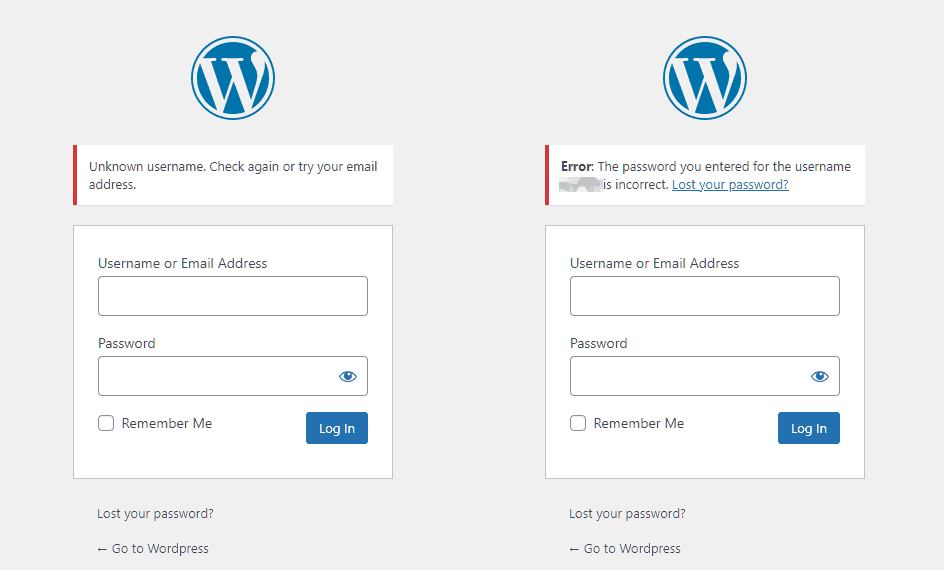
The problem in this case is that we are providing important information to someone who wants to attack our website. In fact we are telling them that the username they are trying to enter with exists or not. Consequently, the attacker will continue to use that username or try another one.
It is advisable to eliminate these warnings for the principle we talked about before: “security by obscurity”. We will try to give as little information as possible to the attacker by hiding these alerts.
To hide these alerts we must add a function inside the file functions.php:
function hide_wordpress_login_errors(){
return 'Gli errori di login sono stati nascosti per ragioni di sicurezza';
}
add_filter( 'login_errors', hide_wordpress_login_errors );
Obviously you can customize the error text however you like.
Protect Files and Functions
WordPress has some features that not everyone knows about, and therefore not everyone uses such as File Editing (you can edit the theme and plugins directly from the admin interface) or XML-RPC which is used to manage WordPress remotely and can be potentially harmful.
Also, some hosting features should be disabled. We’ll see how to avoid running php files uploaded inside the uploads folder and how to hide some files to protect them to the maximum and thus succeed in securing WordPress.
Hide wp-config.php and .htaccess
This operation is very simple to perform, but if you make some mistake your site can become inaccessible. So as always, before performing this operation perform a backup.
You must edit your .htaccess file by adding this code to hide the wp-config.php file:
<Files wp-config.php> order allow,deny deny from all </Files>
In this way you are blocking access to the file. You can use a similar code to hide the same .htaccess file
<Files .htaccess> order allow,deny deny from all </Files>
It is also suggested to lock the installation files for added security:
#Block installation files <files install.php> Order allow,deny Deny from all </files> <files setup-config.php> Order allow,deny Deny from all </files>
Hide WordPress Version
Hiding your WordPress version follows the “security by obscurity” principle we talked about earlier. The less known about your site and your configurations, the better. If you can tell from the code that you’re using an old version of WordPress, it’s like welcoming hackers. Obviously, it’s advisable to keep WordPress updated to the latest version, but hiding the version remains a good practice to secure WordPress.
To hide the WordPress version you just need to add the following function to the functions.php file of the WordPress theme you’re using:
function wp_version_remove_version() {
return '';
}
add_filter('the_generator', 'wp_version_remove_version');
Another place where you can see the version is the readme.html file that is shown in the root of your WordPress installation. This file is included in all versions of WordPress and you can delete it without any problems via FTP or from the cPanel file manager. del cPanel.
If you are using WordPress 5.0 or higher you don’t need to delete this file as the version number is no longer included in the readme file.
Disable File Editing
WordPress has by default a code editor that allows you to edit plugin and theme files directly from the admin interface. This can be a problem since anyone with admin access will be able to add php code.
You can easily disable this feature by adding this code to the wp-config.php file on your account:
// Disallow file edit define( 'DISALLOW_FILE_EDIT', true );
If you want to restrict permissions even more, you can prevent users from installing themes and plugins by adding the following line to the wp-config.php configuration file:
define('DISALLOW_FILE_MODS',true);
Disable execution of PHP files in some folders
Some folders do not need to run php files, such as /wp-content/uploads/. You can create an .htaccess file and upload it inside the folder for which you don’t want php files to run with the following code:
<Files *.php> deny from all </Files>
We recommend that you also place the same .htaccess file inside /wp-content/plugins and /wp-content/themes.
Disable Directory Index
Some hosting services allow directory browsing, this allows a hacker to see the contents of the folder. To disable this option all you have to do is insert a line of code at the end of the .htaccess file located in the folder where WordPress is installed:
Options -Indexes
Disable XML-RPC
Some hosts disable XML-RPC file by default for security reasons. On SupportHost for security reasons XML-RPC is locked by default, and only accessible from jetpack. If you need to use other services you can contact our support to unlock the access according to your needs. If this is not the case in the hosting service you use you just have to insert the following code in the .htaccess file of your website:
# Block WordPress xmlrpc.php requests <Files xmlrpc.php> order deny,allow deny from all allow from 123.123.123.123 allow from 124.124.124.124 </Files>
Disable REST API
Since version 4.4 the REST API is included in the WordPress core allowing any developer to interact with the site. This has allowed many developers to interact with WordPress, but it has also opened up new possibilities for attacks on your website, specifically DDoS attacks.
If none of your plugins use the REST API you can easily disable them by adding two lines of code to your theme’s functions.php file:
add_filter('json_enabled', '__return_false');
add_filter('json_jsonp_enabled', '__return_false');
More Measures toward WordPress security
HTTPS, SSL Certificate
The most overlooked solution to secure WordPress is to install an SSL certificate and display your site with the HTTPS protocol. A very common misconception is that you only need an SSL certificate if you process credit cards on your website. HTTPS encrypted connection allows you to connect your browser or application securely to a website.
If your WordPress site only uses the http connection, check out our WordPress https guide to make the switch in minutes. In the article, you will also find a video that you can follow step by step.
Let’s look at why the HTTPS connection is important even if your website is not an eCommerce. Many hosts, including SupportHost offer Let’s Encrypt SSL certificate for free.
You need to force the HTTPS connection by editing the .htaccess file by adding these lines of code within the file:
RewriteCond %{HTTPS} off
RewriteRule (.*)$ https://www.dominio.it/$1 [L,R=301]
There are plugins to force HTTPS, but we consider it unnecessary to use a plugin instead of adding two lines of code inside a file.
You will also have to force every new session to use HTTPS secure connection by adding the following lines inside the wp-config.php file:
define('FORCE_SSL_LOGIN', true);
define('FORCE_SSL_ADMIN', true);
Security
Naturally, the first factor to use an SSL certificate for is security. How important is your website’s login information? HTTPS is of absolute importance to use an encrypted connection and not pass any data in the clear. This way you can prevent a hacker from gaining access to your website.
SEO
For some time now, Google has included HTTPS connection as one of the ranking factors. While this is a factor that carries little weight, it doesn’t make sense to ignore it completely.
Trust and Credibility
According to a survey by GlobalSign, almost 30% of visitors expect to see a green browser bar. 77% of visitors are afraid that data could be intercepted during transactions. Seeing the green padlock in the address bar immediately gives a feeling of trust to users.
Chrome Alerts
Since version 68, Google Chrome has started to flag as unsafe all sites that don’t use an encrypted HTTPS connection, regardless of whether they are storing user data or not.
This becomes especially important if most of your traffic comes from users using Google Chrome.
Performance
HTTPS supports the HTTP/2 protocol which results in improved performance. The increase in performance is due to several factors: multiplexing, parallelism, HPACK compression with Huffman encoding, and the ALPN extension.
Add HTTP Headers for Security
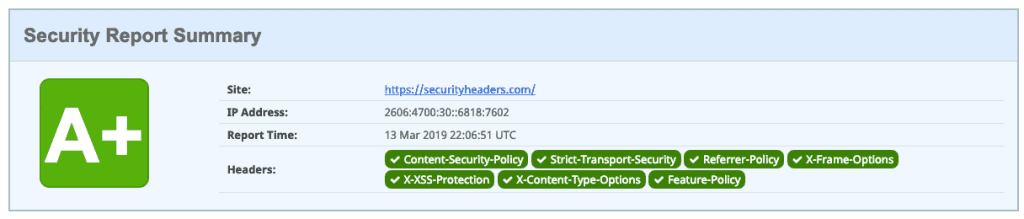
An important element of security for your WordPress site is HTTP headers. These are generally configured at the server level and tell the browser how to behave with the content of your website. There are different types of headers, the most important ones are:
- Content-Security Policy
- X-XSS-Protection
- Strict-Transport-Security
- X-Frame-Options
- Public-Key-Pins
- X-Content-Type
You can check which headers are currently in use on your website with Google Chrome’s developer tools or use the securityheaders.com tool. If you don’t know how to implement them ask your hosting provider, or if you are our customer open a support ticket.
Content-Security Policy
The Content-Security Policy header is used to reduce the risk of XSS by specifying what website content or third-party content can be dynamically uploaded. For example, if you only want to load content from the same domain you would add the following line to your .htaccess file:
Header set Content-Security-Policy "default-src 'self';"
So as to block all scripts from external sources. If instead you want to allow scripts from Google Analytics add this line:
header set Content-Security-Policy "script-src 'self' www.google-analytics.com;"
You need to be careful when inserting headers like this because it is easy to block resources unintentionally and thus create problems. It is always advisable to run tests to make sure everything is working as it should and that we are not blocking necessary resources.
X-XSS-Protection
In order to reduce the risk of XSS attacks, you can also use the X-XSS-Protection header, which helps you protect against this type of attack on older browsers. Add this line to your .htaccess file:
Header set X-XSS-Protection "1; mode=block"
Strict-Transport-Security
This header is used to use HTTP Strict Transport Security (HSTS) which is a mechanism to protect HTTPS connections against “man in the middle” attacks and session hijacking.
With the Strict-Transport-Security header we tell the browser that the site can only be accessed using SSL/TLS encryption.
To enable it we need to add the following line to the .htaccess file:
Header set Strict-Transport-Security "max-age=31536000" env=HTTPS
X-Frame-Options
X-Frame-Options header prevents your site from opening in a frame or iframe thus preventing clickjacking attacks on your website. This type of attack could reveal confidential user data on a seemingly normal site. By inserting the following line into your .htaccess file you tell the browser that frames can only be opened from the same domain or source:
Header set X-Frame-Options SAMEORIGIN
If your site uses third-party services you can specify the allowed domains, denying access to all others, for example:
Header set X-Frame-Options "ALLOW-FROM https://allowedsite.com/"
Public-Key-Pins
HTTP Public Key Pinning (HPKP) is a security mechanism designed to protect websites from impersonation using fraudulent certificates issued by corrupt or compromised certificate authorities.
On the first connection attempt, the client learns which public keys are secure to connect to a particular host. Upon connection, the client checks whether the certificate chain for SSL/TLS transmission contains a public key previously received via HPKP. If not, an error message is returned and the connection is not established.
X-Content-Type
The last header you can add to your website is X-Content-Type which is used to protect your website from loading unwanted stylesheets and scripts. To use this header add the following line of code to your .htaccess file:
Header set X-Content-Type-Options "nosniff"
Server file permissions
The permissions of your installation files (and all files on the server, but in a shared environment you only have access to your account files) are crucial to secure WordPress.
If the permissions are too “wide” anyone can access your files and enter your website. If they are too restrictive your site will not work. That’s why it’s important to set the right permissions for each file or folder.
You can use a free plugin like iThemes Security to scan the permissions of the files on your WordPress site.
Generally speaking all files should have their permissions set to 644 or 640 with the exception of wp-config.php which should be set to 440 or 400.
All folders should have permissions set to 755 or 750. No folders should have permissions set to 777.
Prevent hotlinking
Hotlinking is when you use an image on your site, but that image is hosted on another website. Basically you use the url of an image found online instead of uploading the image to your account. This process steals traffic from the site hosting the image. It may not seem like a big deal, but it can generate some big costs to the person hosting the image.
For example, if a site with a lot of visitors hotlinks your images it can generate large costs or run out of monthly traffic and take your account offline.
To prevent hotlinking in apache you just have to insert this code in .htaccess:
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?yourdomain.com [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ https://dropbox.com/hotlink-placeholder.jpg [NC,R,L]
In the above code you should replace yourdomain.com with your domain name and instead of dropbox url insert a url (external to your account) of an image you want to show instead of your website image.
Hide PHP Alerts and Notifications
Following the principle “Security by Obscurity” it is a good idea to hide PHP errors. These errors can provide useful indications to a hacker who intends to attack your website.
In the development environment these errors are useful to validate your work and discover errors in the code, but on a production website these errors must be disabled in order to hide paths, versions, file names and so on.
To disable these errors all you have to do is add these two lines to the wp-config.php file of your WordPress installation:
error_reporting( 0 ); ini_set( 'display_errors', 0 );
Hide Apache and PHP Information
Often among the information that the server sends in the headers are included information about the software installed on the server and the PHP version used.
You can avoid showing shared server information by adding the following line in the .htaccess file of your website’s root folder:
ServerSignature Off
To not show the PHP version you must instead insert this line inside your .htaccess file:
Header unset X-Powered-By
Keep everything separate
Although we sell multi-domain plans, such as WordPress hosting and semi-dedicated hosting, we recommend that you keep your sites separate as much as possible.
Sites hosted on the same account are subject to a particular vulnerability: if one of your sites gets hacked, it’s very easy to hack all the other sites on the same account, something that happens quite frequently.
If your sites are on different accounts, our protections prevent this from happening, so if one of your sites gets hacked all the others are safe.e, in questo modo se uno dei tuoi siti viene bucato tutti gli altri restano al sicuro.
At this point, you’re no doubt wondering what the point of a multi-domain plan is. We recommend keeping all sites together in such cases:
- you have many small sites and are looking to save money
- they are staging sites, perhaps not reachable from the outside without changing the host files
- you are an expert and are sure that your sites will not be hacked, and if it happens, you know how to clean them and fix them quickly
As a general rule, if you have an important site, our advice is to host it on a separate plan for security reasons.
Conclusion
If you’ve followed our guide, you’ll have realized that WordPress security is a process that involves continuous effort. Keeping everything up to date, limiting access and changing passwords regularly are just some of the things you need to do to protect your site.
Attacks and hackers are always lurking, so in addition to trying to keep everything under control always make sure you have a backup available so you can restore your site in case a hacker has compromised it.
What measures do you use to protect your site? Let me know in the comments below.





Leave a Reply