A SPAM campaign is underway, an email is sent that looks like it’s from cPanel, indicating that your account is close to its space limit.
The email contains one or more links to a phishing site, which replicates the cPanel login page.
Once the cPanel login details are entered they are saved by spammers, and the user is redirected to the real cPanel, and logged in correctly, this way the user doesn’t notice anything.
Let’s see exactly how it works and how we can defend ourselves from this.
Table of Contents
What is phishing?
Phishing (in this specific case cPanel phishing) is a scam that takes place on the Internet. In this type of scam, the scammer tries to trick the victim into giving him personal information.
This is achieved by sending the user to a login page that looks identical to the real login page.
Often, as in this case, an email is sent indicating a problem that needs to be solved.
The unsuspecting user clicks on the link in the email and is redirected to a login page identical to the one the user is used to login.
The user enters her login data, which is saved by the scammer, and is redirected to the real service and logged in, so that they do not realize that their data has been compromised.
What is happening in these days? cPanel phishing
Such scams had already happened in the past, where spammers sent emails to do cPanel phishing.
This time, judging by the number of emails we have found and the number of contacts we have received from our customers, we have reason to believe that this is a major attack.
- Emails are sent mainly to info@domain.com
- Emails are not recognized by antispam software.
- The site that collects the data is always different.
- The servers that send the spam are always different.
This is a carefully crafted campaign, we think that there is a team behind it, and they are likely to make big problems soon.
In this specific case the user receives an email like this:
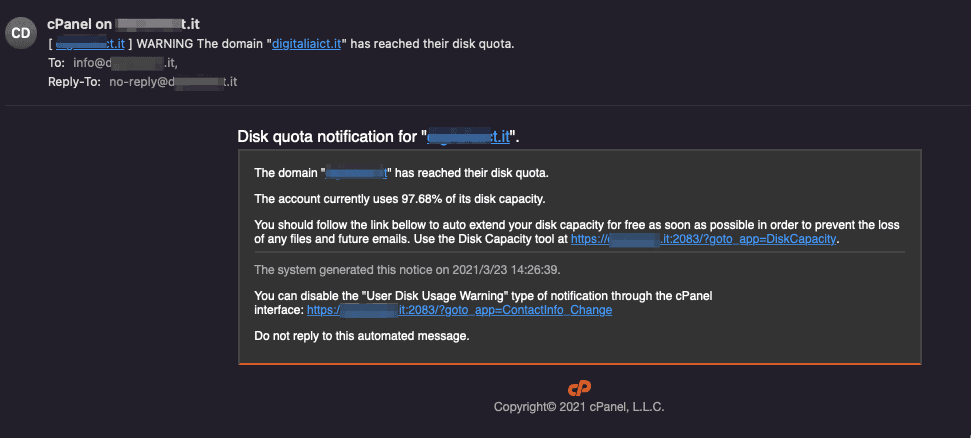
We can see that the spammer provides us with two different links, pointing to the same (fake) login page.
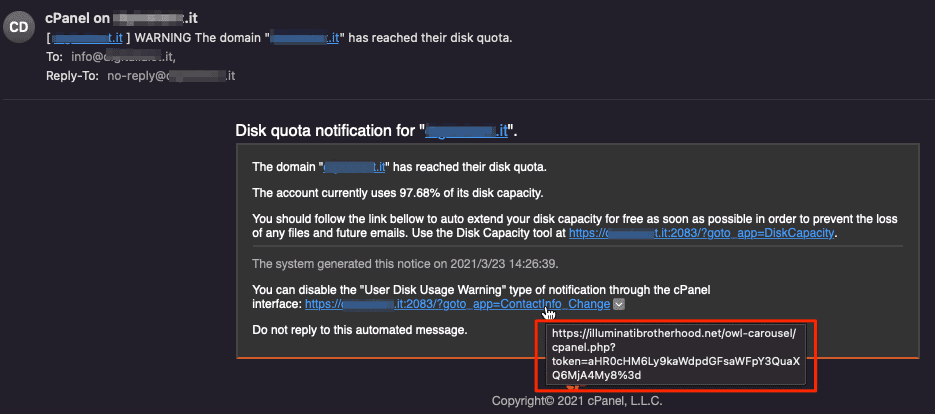
As we can see, the url has nothing to do with the user’s website.
If we check well we can see that it’s actually a hacked website that is used for phishing.
The token is nothing else than a base64 of the url. This is used to redirect the user after the login data are sent, in order to allow the login in the real control panel.
If we click on that link, the user is redirected to the fake login page:

This page is identical to the cPanel page, the only way to tell if it’s the real page or not is to check the address bar.
In this case we see an address that has nothing to do with our website.
If in fact you want to connect to a SupportHost cPanel the link to the cpanel will be domain.com:2083 where domain.com is the name of your domain.
The content of these emails
Let’s see how these emails are set up, this way you know that if you receive such an email it’s probably spam.
So far the emails we have encountered were all identical, the only difference being a slightly different used space percentage, and of course a different domain name.
The mail is sent from this address, and contains a reply-to header to the same address:
no-reply@domain.com (dove domain.com è il domino che cercano di attaccare)
Subject:
[ domain.com ] WARNING The domain "domain.com" has reached their disk quota.
Corpo della mail (ha una grafica identica a quella di cPanel, il testo che abbiamo finora è questo:
Disk quota notification for "domain.com". The domain "domain.com" has reached their disk quota. The account currently uses 98.86% of its disk capacity. You should follow the link bellow to auto extend your disk capacity for free as soon as possible in order to prevent the loss of any files and future emails. Use the Disk Capacity tool at https://domain.com:2083/?goto_app=DiskCapacity. The system generated this notice on 2021/3/23 15:48:53. You can disable the "User Disk Usage Warning" type of notification through the cPanel interface: https://domain.com:2083/?goto_app=ContactInfo_Change Do not reply to this automated message.
If you received emails with different text let me know in a comment to update this article.
How to defend against phishing
Phishing targets the inexperienced user, or the experienced but distracted user.
Unfortunately this phenomenon is very common, periodically we receive emails about problems with PayPal, with a credit card, with the bank account and the likes.
Defending yourself from these online scams is very easy, just don’t click on any of the links that come in by email.
Or check the address bar after clicking, but the solution above is undoubtedly safer.
Did you receive an email indicating a problem and a link to the solution?
It is possible that it is a legitimate email, as well as a phishing email.
No problem, instead of clicking on the link in the email to check what happened, login to cPanel (or your bank if the phishing email is a different type) as you normally would from your control panel and make sure if it’s a real problem or if it was just a SPAM email trying to steal your login details.
NOTE: it is possible to check if the email is true or not by checking the headers, but for the purpose of this post we won’t go into those details.
What to do if I have entered my login data
If you entered your login data without thinking, we can fix it.
The first thing to do is to change the cPanel password and enable two-factor authentication for cPanel and contact our support.
This will ensure that no one can access your account in the future.
So far, no customer accounts have been hacked, so we don’t know exactly how these spammers are going to use your login details in the future.
They may be interested in using these accounts to send out more SPAM and do more phishing. This way the volume of this phenomenon will be impressive.
They might be interested in searching the database in the case of ecommerce sites, to take all the data of paying customers and continue with other illegal actions.
Unfortunately we don’t know for sure, the only thing we can do at the moment is to avoid mistakes and defend ourselves: don’t give them any access data.
What do we do to defend our customers?
There are only two things we can do to defend our customers from a mistake that could cost them dearly.
We have sent an email to all of our customers to inform them of this situation, so they know that there is a campaign of this type going on.
All accounts are protected with imunify360, which helps us detect malware. We also monitor outbound emails to see if an account is sending spam and can take action as quickly as possible.
Conclusions
We have seen that there is a SPAM/phishing campaign going on that seems to have important dimensions.
If we are not careful it is possible that by mistake we give access data to our cPanel account to malicious people.
We are not sure what is the purpose of these people.
We are sure, however, that this is a large campaign that has the potential to do great damage.
Did you receive one of these emails? Did the text match what I reported in the article? Let me know in a comment, so I can keep this article up to date!
Ready to build your WordPress site?
Try our service free for 14 days. No obligation, no credit card required.



