DDoS attacks are among the most dangerous cyber threats but, what exactly are they and what is their basic functioning?
Here’s everything you should know about a DDoS attack: from the simple explanation to the details on the different types of attacks and how you can defend yourself.
Let’s start with the meaning of the word DDoS.
Table of Contents

What is a DDoS attack?
DDoS stands for Distributed Denial-of-Service.
What does it mean?
In short, a DoS attack occurs when the attacker, a hacker, causes an interruption of the service. When the attack is distributed (DDoS and non-DoS), it means that different sources are used to carry out the attack.
When we hear phrases such as damaging the server or suffering DDoS attacks we are faced with a situation in which the computer system, for example: a server, is receiving so much traffic or requests that it cannot handle them.
The result is that often the machine stops working and the hosted site (or sites) are no longer reachable.
We have made a practical example in the case of a website. However, keep in mind that other systems, such as e-mail servers, can also suffer attacks of this type.
Let’s go into detail on how DDoS attacks work to understand the difference with other types of attacks.
How a DDoS attack works
Unlike a DoS attack, DDoS attacks are more dangerous because they are difficult to counter.
To understand what exactly happens during a DDoS attack, let’s start with a simplified example.
Imagine a logistics center that receives and sorts of goods. In a normal situation, the packages arrive by courier, the workers sort the goods and redistribute them.
If the logistics center began to receive hundreds of packages transported by hundreds of different couriers, the limited number of employees would no longer be able to manage the sorting and the entire chain would be interrupted.
Now imagine that the goods are the visitors to the site, each visitor sends requests to the server involving the use of resources.
As long as there are real visitors and in a reasonable number, the server manages the requests by distributing its resources, just as the logistics center manages the goods thanks to the employees.
When there is a DDoS attack, however, requests are sent from different sources: hundreds or thousands of fictitious visitors send many requests to the server.
Since all the resources of the machine have been overloaded, the server is no longer able to process any requests. The same thing happened in the example of the center, where the employees were no longer able to receive and sort the enormous quantity of goods.
Now that we have seen how this type of attack works in broad terms, let’s get a little more technical.
Why are we talking about DDoS attacks and botnets?
How does the attacker send requests from multiple sources? Taking advantage of what is called a botnet or zombie network.
The hacker constitutes a real network made up of computers and computer systems that he has taken control of. Each machine that is part of this network is called a bot or even a zombie, precisely because it acts without its knowledge.
It is the hacker, in fact, who controls all the bots on the network and to do so he infected the different machines with malware so as to take control of them. Generally the system consists of opening backdoors through which you can remotely control other computers.

This strategy allows the attacker to stay behind the scenes and is therefore more difficult for the attacker to be traced.
The ultimate goal is to exploit bots to send an exorbitant number of requests to a server or computer and cause it to fail. The result is that the attacked machine will slow down because it will be more difficult to respond to all requests and sometimes some requests will not be processed at all.
DDoS vs brute force: what’s the difference?
We have clarified what changes between DoS vs DDoS.
In the case of DoS, the attack is launched from a single source. In distributed attacks, DDoS, multiple machines are used to create a real network and target the victim system.
What is the difference between brute force and DDoS attacks instead?
Another common cyber attack is the one called brute force. This threat uses a completely different mechanism to breach systems.
Brute force attacks rely on attempts to break into a password-protected system. The mechanism that is used is to try different passwords, starting with the most common ones, until you can find the correct combination that guarantees access.
CMSs like WordPress can fall victim to these attacks. Fortunately, there are ways to prevent these intrusions. The sites hosted on SupportHost can count on a system of proprietary anti brute force rules that protect against unwanted access.
What does a DDoS attack involve?
As we said, when a distributed attack occurs, the greatest difficulty lies in distinguishing the “normal” traffic and therefore that generated by real users, from the “illegitimate” one, that is, coming from the bots controlled by the hacker.
Precisely for this reason it is not possible to stem the attack.
But what are the reasons that lead to this kind of cyber attack?
- In some cases it can happen that the hacker carries out a real extortion by requesting a payment with a promise to stop the attack.
- At other times, DDoS attacks are directed towards certain entities or certain countries, for example for political reasons.
- The motivation can also be due to wanting to create economic damage to a competing company.

It is important to know that attacks are not temporary and large ones can last for days, weeks and in some cases even longer periods.
These attacks can, therefore, have important consequences for the company that is the victim:
- if the disservices concern a website, there will be damage to the image because the site will be unreachable;
- in the event that the problem persists for a long time and also extends to the company’s customers, there will be economic losses.
Furthermore, it is good to consider that DDoS attacks can pave the way for intrusions by hackers who exploit the backdoors created by the attack.
If your site has been the target of an attack, in addition to restoring its functionality, you should make sure you get it back safe. Check out our guide on how to improve WordPress security to have a good foundation to start from.
How to protect yourself from a DDoS attack
The risks of a cyber attack are high: disruption, damage to the reputation of the company and economic losses are just around the corner when you fall victim to these threats.
In addition to putting mitigation measures in place when the attack is in progress, the best weapon is prevention. In order to be able to avoid attacks, it is therefore necessary to take security measures to protect the infrastructures.
Among the technologies that can be exploited are firewalls and content distribution networks (CDNs).
Services like Cloudflare, for example, offer an integrated anti-DDoS protection system and can be an ideal solution for high traffic sites.
If you order one of our hosting plans or are already our customer, you will be able to select Cloudflare activation from the additional packages.
Anti DDoS protection: the solutions adopted by SupportHost
Offering a secure hosting service is at the top of our goals. We use perimeter firewalls to protect our servers as well as CSF (ConfigServer Firewall) present on each server.
Firewalls constitute a barrier and are able to carry out checks on incoming packets in order to prevent the passage of invalid and therefore potentially dangerous packets.

In order to guarantee their security, our systems use automatic tools capable of recognizing in advance the most common attack patterns.
This recognition system allows us to block attacks in the bud, before they can take effect and cause disruption to the servers and, as a ripple effect, also to the websites that are hosted there.
Ability to recognize attack patterns and effectively filter traffic
As we explained in this in-depth study, DDoS attacks are particularly effective because they aim to make traffic recognition problematic.
The difficulty is given by not being able to distinguish the traffic generated by real users from that of the bots used to propagate the attack.
Through a traffic filtering system, it is possible to make a distinction between the legitimate and the illegitimate, blocking only the latter. It is in this way that it is possible to block attacks including the UDP flood which we will talk about when we will see what types of DDoS attacks there are.
By using dynamic traffic filters, it is possible to defend against attacks that consist in flooding the server with requests, for example by sending invalid packets. A situation of this type occurs for example during SYN flood attacks that we will have the opportunity to deepen in the next paragraphs.
Being able to identify the patterns under which most DDoS attacks are performed allows us to effectively block the most common attacks and prevent them.
Ability to block IPs
Another important defense tool is the selective blocking of IP addresses.
By default our firewall is configured to block the IP addresses of some countries in order to prevent the sending of unwanted requests.
Additionally, all of our plans use cPanel as their hosting control panel and provide the IP Blocking feature. You can use this tool to block individual IPs and address ranges.
The biggest DDoS attacks ever performed and the current situation
There have been several examples of DDoS attacks involving major companies in recent years.
In September 2017, Google‘s infrastructure suffered the largest DDoS attack with a traffic speed of 2.54 Tbps (terabits per second). The news of the attack was detected only after years, in 2020, as reported by ZDNet.
Equally large was the DDoS attack reported by Amazon and mitigated through the AWS Shield service. The report was made in June, after the threat was unleashed in February 2020. This is the second largest DDoS attack to date and has reached 2.3 Tbps.
The previous ominous record, as shared in their report, belonged to GitHub which in February 2018 suffered an attack with a peak of 1.3 Tbps.
In addition to these cases of extensive attacks, the number of threats spreads and increases every year.
Netscout creates reports on cybercrime trends every year. The most recent data are those referring to the first half of 2022 in which 6,019,888 DDoS attacks were reported.
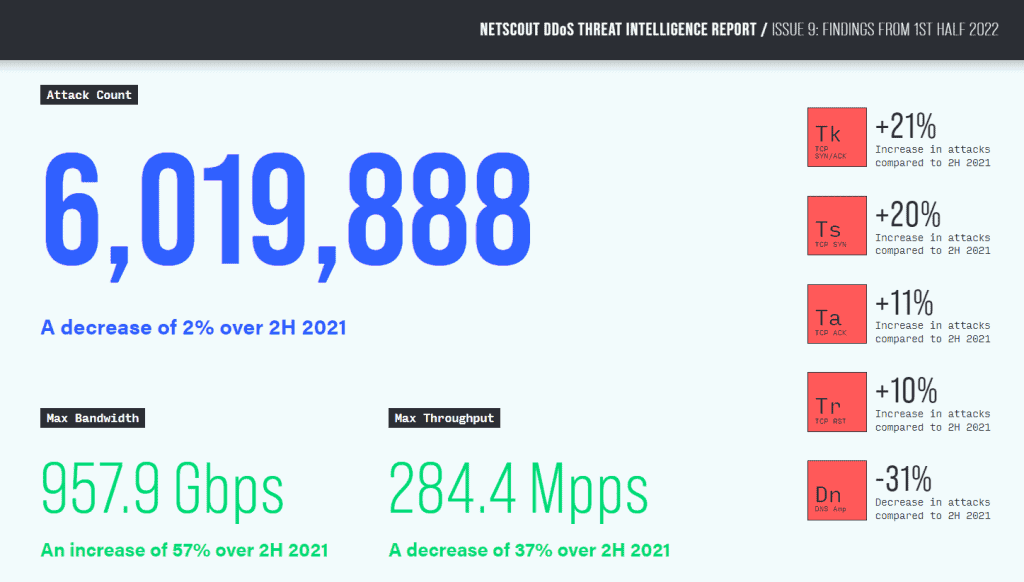
The data shown above comes from the Netscout report on the first half of 2022 and is compared with the attacks that occurred in the second half of 2021. The number of attacks in this case refers to those that have been recorded globally.
How many types of DDoS attacks are there?
When we talk about DDoS, we are actually referring to different types of attacks based on the method used.
We talk about:
- volumetric DDoS attacks;
- attacks on protocols;
- application-level attacks.
To understand how these types of attacks differ, we need to open a little parenthesis on how networks work.
What is the OSI model?
The OSI (Oper Systems Interconnection) model, also known as ISO / OSI because it was created by the International Organization for Standardization (ISO), is a standard model that establishes the way in which connections occur in the network.
This model serves to explain the structure of the network and consists of 7 levels, for each of which there is a communication protocol.
1. Physical layer: at the base of the structure there is the hardware and therefore the “physical” components that allow the connection. Example: modem. Example of technology: OTN (optical fiber).
2: Data Link or Datalink Layer: The next layer allows data to be transferred over the physical link. Example: bridge to connect two local networks. Technology example: ethernet.
3: Network or Network Layer: this level is used to define the passage of data and the physical path that they will have to follow, therefore it deals with routing also known as communication routing. Example: router. Protocol example: IP.
4: Transport or Transport Layer: the data must be sent and before sending divided into packets, that is to say small portions that can be transmitted more easily. Protocol example: TCP and UDP.
5: Session or Session Layer: a session is created at this level in order to maintain communication between different applications. A check is also performed so that packets are transmitted without errors and can resume from a checkpoint when they occur. Protocol example: SOCKS.
6: Presentation or Presentaton Layer: it is in this layer that the data cryptography and compression systems operate. The transferred data must in fact be encoded and then decoded.
7: Application or Application Layer: it is the highest level and therefore the one in which we find the protocols used in direct contact with the applications. For example when a user wants to access a server terminal he can do so using the SSH connection which operates right at the application level.
Other examples of protocols acting at this level are:

Now that we’ve outlined how communications work, let’s see what kind of DDoS attacks can be performed and how they interfere with data transmission.
Volumetric DDoS attacks
The most frequent and used distributed denial-of-service attacks are volumetric ones. The attack consists in sending requests and “dummy” traffic to ensure that all the bandwidth is saturated.
Due to the sudden spike in traffic, visits from real users who will find themselves in front of error pages or will not be able to access online services will be blocked. The site or application involved will be unreachable.
Several specific examples belong to this category, such as:
- UDP flood;
- DNS amplification;
- ICMP flood.
UDP flood attacks use the UDP protocol to send packets, in response the target of the attack will have to send packets to communicate that the “destination is unreachable“. This will exhaust the resources and bandwidth available to the system that is under attack.
Attacks on protocols
When a DDoS attack is directed towards a network protocol it is referred to as a protocol attack.
The mechanism behind these attacks is shared by multiple specific cases such as SYN flood attacks and Smurf DDoS attacks.
Let’s understand how a SYN flood attack works.
During a TCP connection these three steps take place:
- the client sends a SYN packet to the server;
- the server sends a SYN-ACK packet to the client in response;
- the client sends an ACK packet.
In SYN flood attacks, clients are used to send “SYN” packets, while ACK response packets are never sent.
This causes the server to listen for missing ACK packets and keep the TCP connection open. As a result, the server’s resources are saturated and it is no longer able to handle real and “legitimate” requests.
Application-level attacks
In these cases, DDoS attacks target systems operating at the application level and are, in fact, also referred to as level 7 DDoS attacks.
An example is HTTP flood attacks in which GET or POST requests are sent to a web server. In fact, there is talk of HTTPS GET Flood and HTTP POST Flood attacks.
The purpose is to send requests to be able to occupy all the resources of the server and to stop normal operation.
Conclusion
We have seen that DDoS attacks can be extremely dangerous and lead to disruption and economic losses.
After examining how these types of attacks work and how to defend themselves, we went into detail by seeing how they are classified into different types and how they manage to interfere with network communications causing malfunctions.
Terms like DoS, DDoS, and botnet should sound more familiar to you at this point. Is everything clear or do you have any doubts? Let us know in the comments.





Leave a Reply