In this guide I’ll explain what SSH is and what it’s for.
We’ll then look at the various ways to establish an SSH connection to a remote server, and we’ll perform an SSH login with a password and an SSH login with a key, after seeing how to create an access key.
I also explain how to make the server more secure from bruteforce attacks by disabling password access and changing the default SSH port to a custom one.
But without further ado let’s get into the topic, what is SSH and what is it for?
Table of Contents
What is SSH
SSH stands for Secure Socket Shell. The protocol was created in 1995 by a Finnish university researcher. The second version was created 10 years later and to date it has no vulnerabilities.
This protocol allows system administrators to securely access a remote computer. As a command interpreter, it allows system administrators to issue commands and launch applications.
Basically, this protocol allows us to establish a remote session with another computer using a command line interface.
Origins and history
SSH was designed by Tatu Ylönen in 1995, who as I said at the time was a Finnish university researcher. At the first version, which was called SSH – 1, were found several defects, corrected with the second version that was adopted as standard in 2008.
Version 2 is not compatible with the first version and uses stronger integrity checking in order to improve security.
What is possible to do with SSH?
In a word: everything.
Through SSH we issue commands to the server using the Shell Scripting language.
These shell scripts are run by linux kernel interpreters. The most common interpreter is bash, but there are others like csh and zsh.
You can do everything through bash. Install applications, update them, remove them, check the configuration, see what processes are active, etc.. In practice a linux system can be controlled entirely from the command line, and then via SSH.
SSH connection
To connect with SSH to a remote server we just need the terminal of Linux or Mac OSX, if you use Windows you will need an SSH client like putty, which I will talk about later in detail. In the case of Linux you can connect to SSH even if you use a live distribution, for example with Ubuntu on USB.
Our semi-dedicatedhosting, WordPress hosting, VPScloud hosting and dedicated servers include SSH access. In the case of shared hosting, however, you can purchase the service separately for an additional fee.
In this article I’ll discuss two different ways to connect to a remote server with SSH: with a password and with a key.
If we want to connect with SSH to the server we will need the following data:
- Server IP address.
- User name (can be root or another user name).
- Port (usually 22, in our services we use 2299).
- Password or key (depends on how you want to connect to the server, in the next paragraphs I’ll explain it in detail).
SSH access with password
The easiest way to SSH connection is password access. We basically connect with a user and password. The user can be root if you have an unmanaged service or another username, for example the username and password you use to log into cPanel if you want to connect with SSH to your semi-dedicated hosting.
To connect via ssh with the terminal of Mac OSX or Linux just run this command
ssh username@hostname -p portnumber
Which with real data becomes this way:
ssh root@123.123.123.123 -p 2299
As I said on our servers we use port 2299. Note that if the server you want to connect to uses port 22 it doesn’t matter to write “-p 22” since it is the default port.
As soon as we send this command the terminal asks us if we are sure we want to connect.
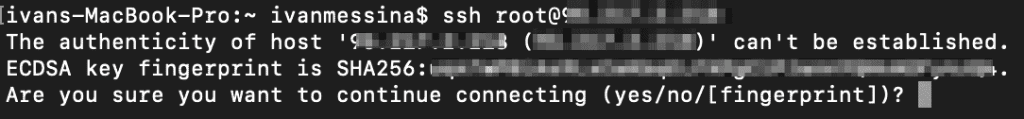
This message tells us that we have never connected to this server before, so this is completely normal. If you have connected to this server before (with the computer you are using now) and you see this message it can mean two things:
- the server has been configured with a new key
- someone is forging the identity of your server
If you see this message it’s possible that the server is warning you of a man-in-the-middle attack, you’ll have to evaluate on a case-by-case basis. But as I said if it’s your first connection it’s completely normal.
At this point we type yes and press enter to continue, and we are prompted for the password. Note that while you are typing the password you will not see any feedback on the screen, once you are done entering the password press enter.

At this point we are in. We see in fact the name of the server and no longer the name of our computer. We see in fact that we are connected as root to the server called centos-2gb-hel1-1:
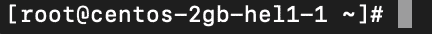
Pretty easy, isn’t it? So let’s see how to connect using a key.
SSH connection with key: creating keys
The keyed connection is the most secure way to connect to a server and should be the standard. We are forcing this system on new servers for security reasons.
With this system we have two keys, one public and one private, which are used to create an asymmetric encryption system. With this encryption, messages are encrypted and decrypted with different keys.
As the name implies, private keys are secret and maintained only by the owner and have a password. These keys are used to prove one’s identity.
Public keys are public, and they are distributed to all servers with which you want to communicate securely.
The two keys have a mathematical dependence, but it is impossible to derive the private key from the public key. They also have another quality: data encrypted with the public key can be decrypted only by the private key and vice versa.
After this brief explanation of how keys work, let’s see how to use this method step by step.
Creating a pair of keys on Mac OSX and Linux
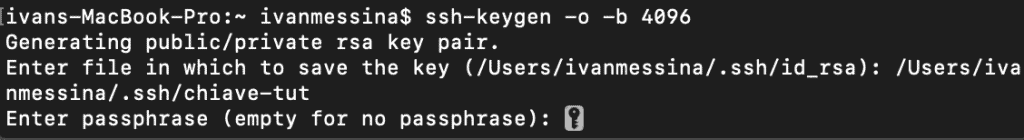
We open the terminal and type the command:
ssh-keygen -o -b 4096
Press enter to generate the key. The “-o” option was added in 2014, if it gives you an error remove it and try again.
At this point we are asked where to save the key:

If it’s the first key you’re creating you can leave the default position, otherwise enter a position to not overwrite your key. In any case don’t worry, before overwriting your key you are asked for a confirmation, so the possibility of overwriting your key by mistake is remote.
Since I already have a key but I want to create another one for this tutorial I decided to put it in . ssh and call it key-tut.
At this point we press enter and you will be asked to enter a passphrase for the key. You can simply press enter and leave it without a passphrase, but for security I recommend that you enter a password. Choose one that you remember because you will be asked for it every time you connect with SSH to the server using your key.
After pressing enter it will ask you to type the key again for confirmation, then press enter again to generate the key.
Creating a pair of keys on Windows
Download PuTTYgen to your computer and open the application.
Select RSA, set the number of bits to 4096, and click “Generate”.
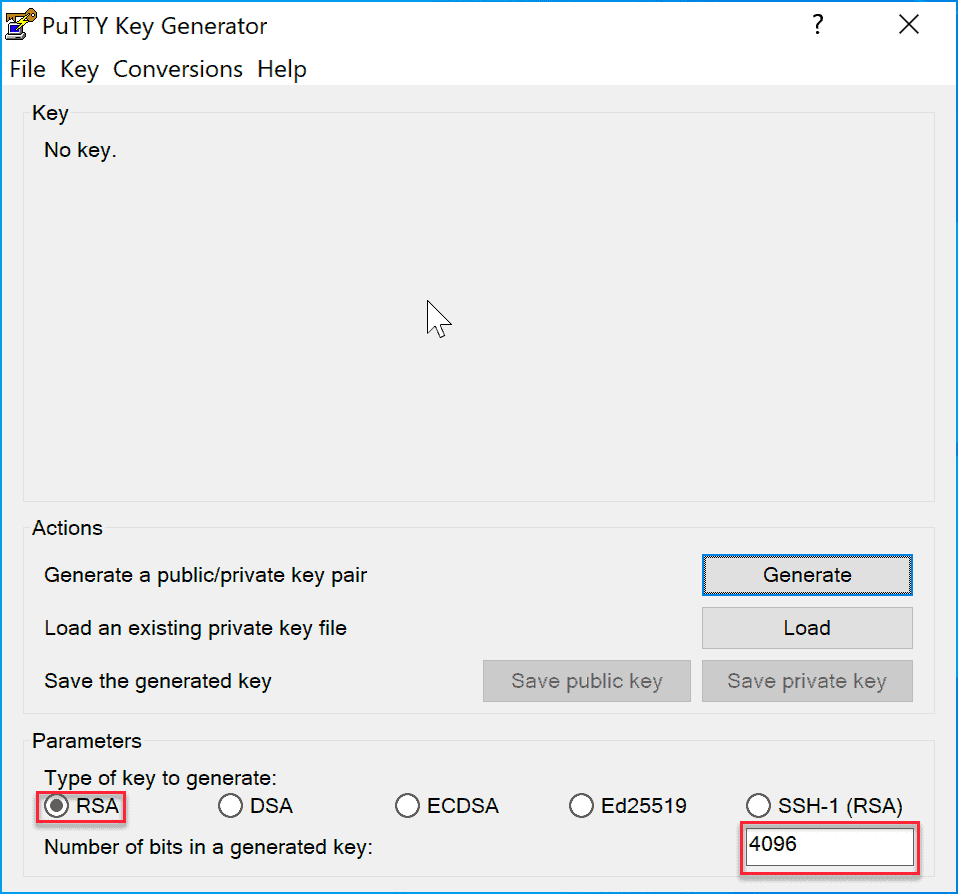
Move the mouse in the empty area to generate “randomness”:
The two keys are generated:
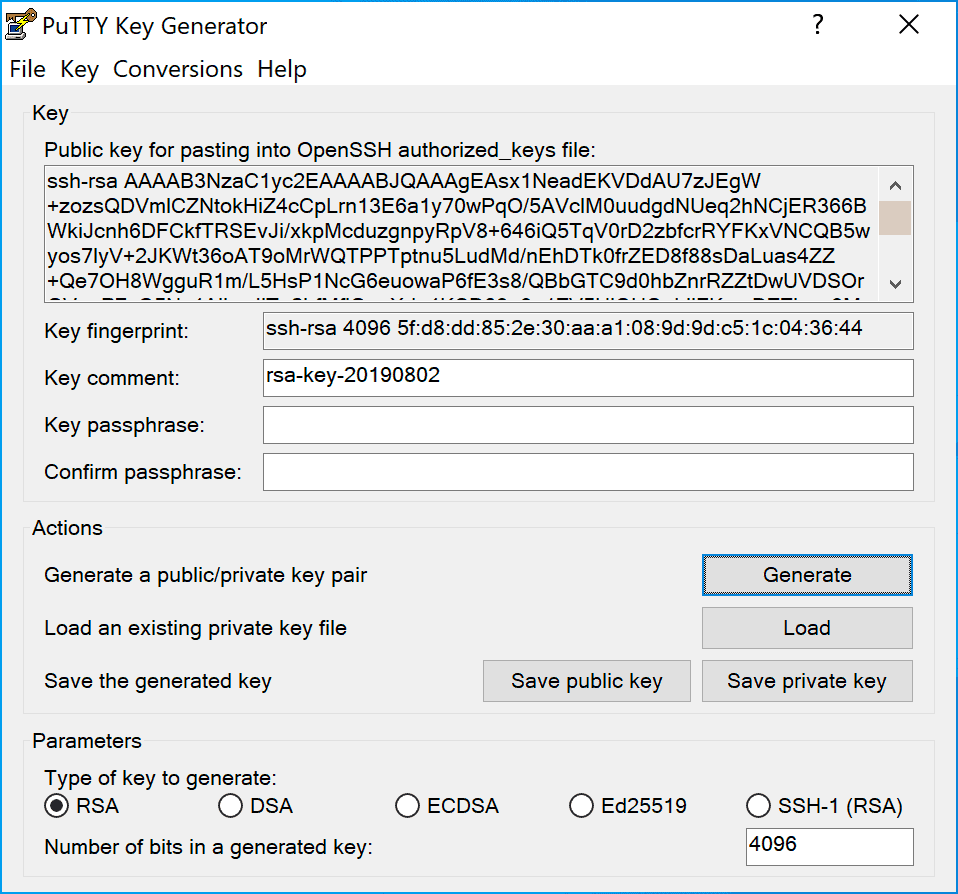
Enter a comment for the key, then save the private key and the public key in a folder of your choice, save them in the same folder. Copy the text of the public key, you’ll need it shortly.
Now we have generated our keys, what is the next step to connect to the server via SSH?
Adding the key to the server
If you have a managed hosting or dedicated plan with us you can’t add the key because you don’t have root permissions. You will have to send us your public key and we will take care of adding it to the server.
If you have root access I need to add your public key to the server, there are several ways to do this.
Copying public keys to server using ssh-copy-id
ssh-copy-id is a tool that is present by default on many systems, we’ll try this method first for its simplicity.
In order to use this method you must have password access to the server. What you will have to do to use this command is to specify the host and user (to whom you have password access) for whom you want to add the key.
ssh-copy-id username@remote_host
You may receive this error:
/usr/bin/ssh-copy-id: ERROR: No identities found
This is because the default ssh-copy-id command looks for the key is_rsa.pub, as stated in the man page:
If the -i option is given then the identity file (defaults to ~/. ssh/id_rsa.pub) is used, regardless of whether there are any keys in your ssh-agent. Otherwise, if this: ssh-add -L provides any output, it uses that in preference to the identity file
If you used another name you will have to use the -i option of the command like this:
ssh-copy-id -i nomechiave.pub username@remote_host
The system prompts us for the user’s password to login, and enters the key.
Where is the key inserted? Let’s look at that in the next section.
Copying the key using SSH
The question that arises is: where is this key saved on the server when we use the ssh-copy-id command? The key is saved in:
~/. ssh/authorized_keys
We can then navigate through the folders, and edit the authorized_keys file by adding our public key.
To view our public key we can use the command (on our local computer):
cat ~/. ssh/id_rsa.pub
We will get a result like this:
ssh-rsa wxIxvcBF8PXSYvobFYEZjGIVCEAjrUzLiIxbyCoxVyle7Q+bqgZ8SeeM8wzytsY+dVGcBxF6N4JS+zVk5eMcV385gG3Y6ON3EG112n6d+AAAAB3NzaC1yc2EAAAAABAAACAQCqql6MzstZYh1TmWWv11q5O3pISj2ZFl9HgH1JLknLLx44+tXfJ7mIrKNxOOSMXN0PPB5CnhHf7ovgy6nL1ikrygTKRFmNZISvAcywB9GVqNAVE+ZHDSCuURNsAInVzgYo9xgJDW8w0pHtACr7kvS46itMosi/uS66+PujOO+xt/2FWYepz6ZlN70bRly57Q06J+ZJoc9FfBCbCyYH7U/ASsmY095ywPsBo1Rfz3K2B+ZVIpSDfki9UVKzT8JUmwW6NNzSgxUfQHGwnW7kj4jp4AT0VZk3ADw495mDOeCSq5Uw2o8U77+xiFxY0OEBIcO6x+PnUSGHrSgpBgX7Ks1r7xqFa7heJLLt2wWwkARptX7udSq05paBhcpB41XQ9Pqhn7M2G/12gI5QSZX3Iq7YLMgeksaO4rBJEa54k8m5wEiEE1nUhLuJ0X/vh2xPff6SQ1BL/zkOhvJCACK6Vb1N1/YOorJ068foQDNVpm146mUpILVxmq41Cj55YKHEazXGsdBIbXWhcrRf4G2fJLRcGUr9q8/lERo9oxRm5JFX6TCmj6kmiFqv+Ow9gI0x8GvaQ== demo@test
Now we connect to the server using the method we prefer and enter our public key in the file ~/. ssh/authorized_keys
We can do this through an editor like vi:
vi ~/. ssh/authorized_keys
Or using this command to add our key to the file:
echo public_key >> ~/. ssh/authorized_keys
In this command you will have to change “public_key” with your public key, with a simple command you can add your key to the file without the need to open the file with an editor and edit it.
SSH linux connection
Now we come to the point of the article, how to perform SSH connection with Linux?
We open the terminal and type the command:
ssh user@123.123.123.123
If there is a key “~/. ssh/id_rsa” the system will try to connect with the key. If the key you created has a passphrase this will be requested, otherwise you will connect directly.
Otherwise, it will prompt you for your login password.
If you have set the key correctly and it asks you for the password, the problem is due to the fact that your key has a different name than the default name, which is id_rsa.
If you use a key with a different name, you must specify the name and location of your key in the command:
ssh -i ~/username/nomechiave user@123.123.123.123
If you try to connect to one of our services, it will use port 2299. As I said before this command tries to connect to port 22, so if you try to connect with SSH in this way to one of our servers you will get an error:
ssh: connect to host 95.217.2.218 port 22: Connection refused
For this we need to use the “-p” option to specify the port in this way:
ssh user@123.123.123.123 -p 2299
To summarize, depending on the case you may need to use this command
ssh -i ~/username/nomechiave user@123.123.123.123 -p2299
Mac SSH Connection
If you use Mac and you want to SSH access to your remote server, the procedure is identical to linux, since both systems use the terminal and have many similarities. You can refer to the paragraph above: SSH Linux connection.
SSH Windows connection
Since on Windows you don’t have a terminal you need an application called Putty. Once you have downloaded and installed it, run it.
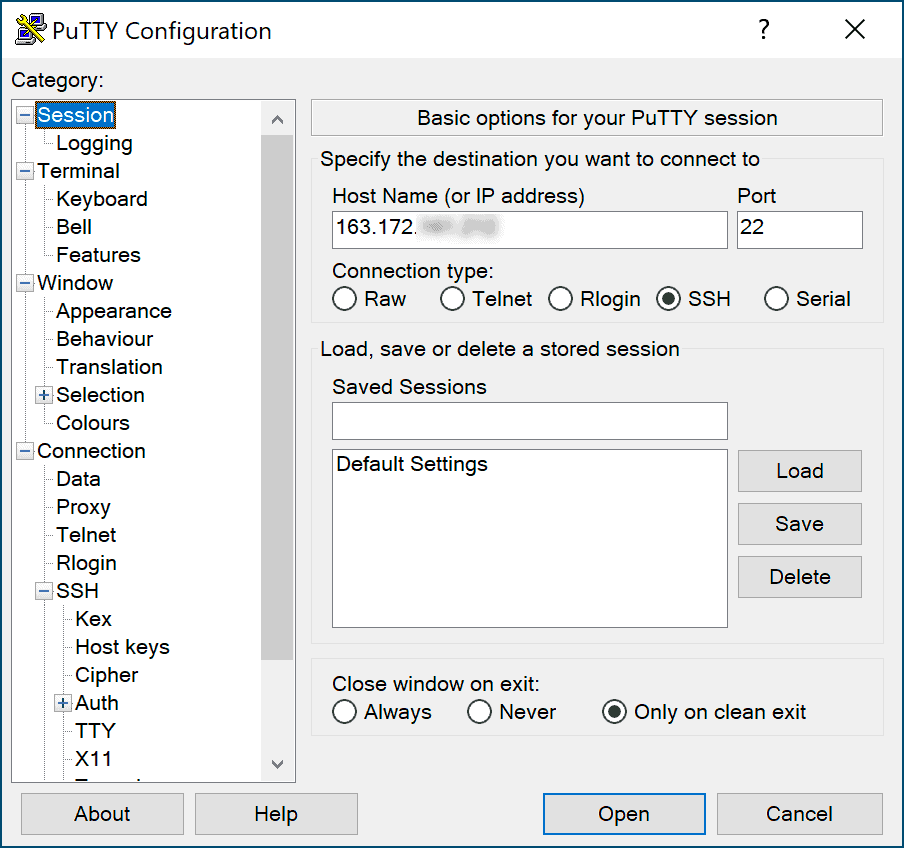
Enter the correct hostname and port:
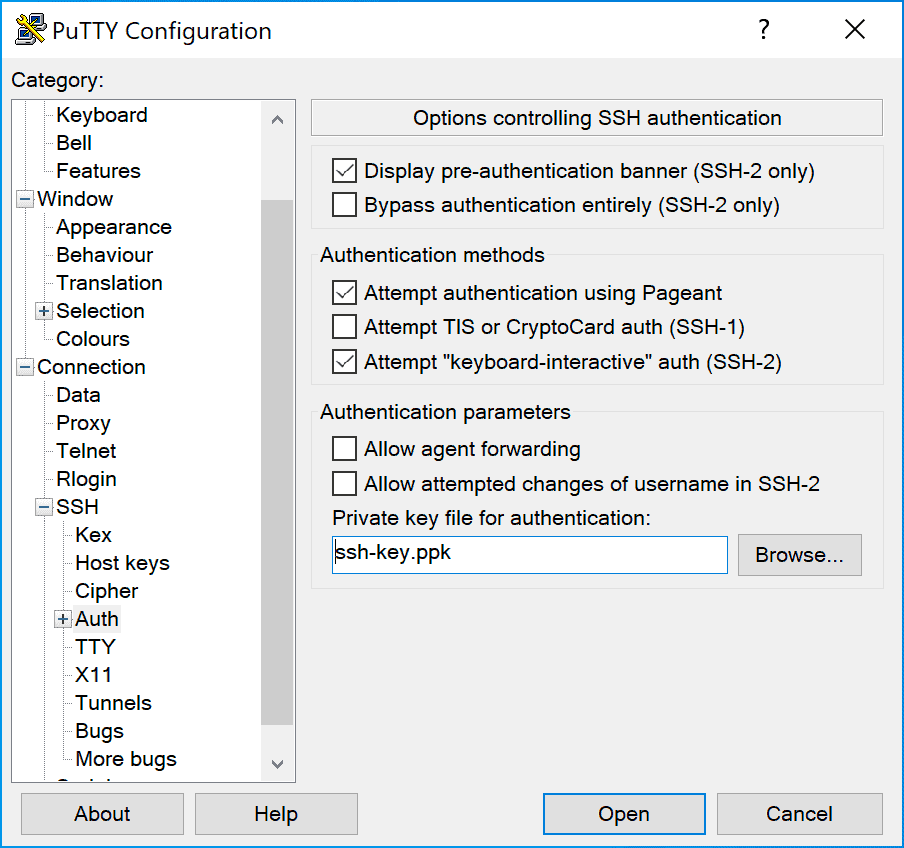
Then in the sidebar expand the Connection -> SSH section, select the Auth subcategory and click Browse and select the access key you generated earlier:
Then click on Open to connect to the server.
If this is the first time you connect to the server you will see this message:
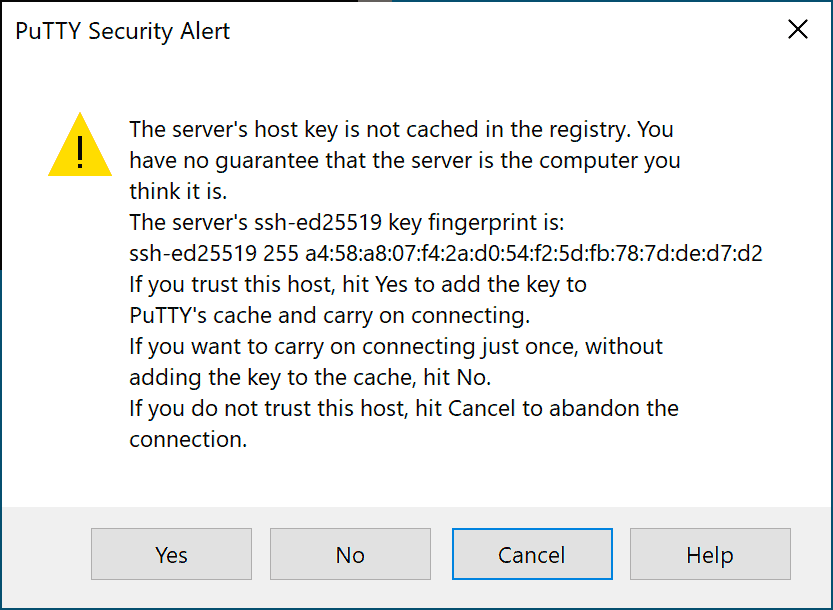
Press ok to confirm, the terminal will open, asking you for your username, enter your username. Now you are connected with SSH on the server.
Advanced Operations
Once you first connect to the server, there are a few steps you can take to make it more secure.
Disable password authentication to the server
If you were able to log in with the key to the server without any problems, it means that you were able to configure the keys correctly.
However, password authentication remains active, which means that your server could be the victim of a bruteforce attack.
Before doing this make sure that you have set up key access to the root account on your server, or that you have given key access to an account with sudo privileges.
Log in to the server with root account and edit the ssh configuration file:
vi /etc/ssh/sshd_config
Or log in as a user with sudo privileges and run this command:
sudo vi /etc/ssh/sshd_config
Edit the file by setting:
...
PasswordAuthentication no
...
Then save and restart the sshd service, I will explain how to do it in a later paragraph. This operation is necessary to apply the changes.
Change SSH port
Again, as above, we need to edit the sshd configuration file using the command:
vi /etc/ssh/sshd_config
let’s look for this piece of code:
#Port 22
Note that there may or may not be a hash character in front of “Port”. The hash mark indicates that the line is a comment, and is therefore ignored.
Delete the hash character if present and replace port 22 with another number between 1024 and 65536 and save the file.
Also in this case to apply the changes it is necessary to restart the sshd service.
Restart sshd
Once you have made these changes you will need to restart the sshd service for them to take effect.
If you use Ubuntu you can run the command:
service ssh restart
If you’re using CentOS instead you have to use the command:
systemctl restart sshd
Conclusions
In this article we saw how to connect to the server using user and password, but we also saw how to create a key, add it to the server and connect using our key.
We also saw how to disable SSH access with password and how to change the port for SSH connection.
Were there any steps that were unclear? Were you able to successfully connect using SSH with your key? Let me know with a comment.


Leave a Reply